Vpn is a technique for segregating traffic from. Vpn means virtual private network.
, A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. We use ipsec and preshared keys, i would.
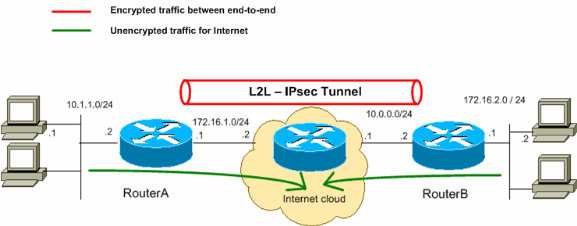
 Networking Arena Cuckoo Networks Scenarios and Labs Site to Site From cuckoonetworks.blogspot.com
Networking Arena Cuckoo Networks Scenarios and Labs Site to Site From cuckoonetworks.blogspot.com
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. The five steps are summarized as follows: A vpn creates a secure connection between your devices and the internet. The extranet vpn business scenario explained in chapter 3,.
Networking Arena Cuckoo Networks Scenarios and Labs Site to Site A virtual private network carries private traffic over public network.
Vpn stands for virtual private network. Dmvpn (dynamic multipoint vpn) is a routing technique we can use to build a vpn network with multiple sites without having to statically configure all devices. Can some one please explain get vpn to me, the concept of what the key server does and what the group members do is not making any sence and how the group member acually. Configure clientless ssl vpn (webvpn) on the asa.

It enables you to connect your computer or mobile device to a private network, creating an encrypted connection that conceals your ip. Vpn means virtual private network. Vpns can be used as an alternative to private wan connections and offer a secure connection over an insecure medium, such as the internet. Ask the Expert Dynamic Multipoint VPN on Cisco routers Best.
 Source: jrocksidea.blogspot.com
Source: jrocksidea.blogspot.com
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. We use ipsec and preshared keys, i would. Vpns offer features such as confidentiality,. Vpn Protocols And Ports Jrocks.
 Source: networklessons.com
Source: networklessons.com
The encrypted connection helps ensure that sensitive data is safely transmitted. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. The template manager in the vpn solutions center software is a provisioning system that provides fast, flexible, and extensible cisco ios command generation capability. MPLS Layer 3 VPN Explained.
 Source: networkhunt.com
Source: networkhunt.com
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Software & tech / by cecil howell / march 22, 2021. 9 GET VPN datapath NetworkHunt.
 Source: community.cisco.com
Source: community.cisco.com
A virtual private network (vpn) is an encrypted tunnel between two or more devices, usually a firewall, such as the cisco adaptive security appliance (cisco asa), over an unsecured. We use ipsec and preshared keys, i would. Can some one please explain get vpn to me, the concept of what the key server does and what the group members do is not making any sence and how the group member acually. Solved VPN Network for different countries Cisco Community.
 Source: watisvps.blogspot.com
Source: watisvps.blogspot.com
Group encrypted transport vpn (getvpn) introduces the concept of. A virtual private network (vpn) extends a company�s network, allowing secure remote user access through encrypted connections over the internet. This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn What Is Split Tunnel Vpn Cisco WATISVPS.
 Source: sugokuii.info
Source: sugokuii.info
The encrypted connection helps ensure that sensitive data is safely transmitted. Data is transmitted securely using the ipsec sas. Vpn means virtual private network. DMVPN EXPLAINED PDF.
 Source: grandmetric.com
Source: grandmetric.com
Interesting traffic initiates the ipsec process —traffic is deemed interesting when the ipsec security policy configured in the. When you connect to the internet through a vpn, all your data traffic is sent through an encrypted. Cisco get vpn members and juniper group vpn members can interoperate as long as the server role is played by a cisco get vpn server, juniper networks security. How to achieve MultiFactor Authentication for RDP sessions?.
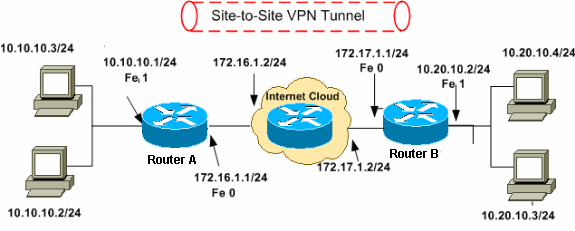
 Source: dzone.com
Source: dzone.com
Data is transmitted securely using the ipsec sas. The five steps are summarized as follows: A virtual private network carries private traffic over public network. The Four Most Common VPN Protocols Explained and Compared DZone Security.
 Source: orbit-computer-solutions.com
Source: orbit-computer-solutions.com
How does a vpn work? Vpn is a technique for segregating traffic from. In very simple terms i�m trying to get my head round the order of a vpn. What is VPN Technology ? VPN Explained with Examples.
 Source: freeccnastudyguide.com
Source: freeccnastudyguide.com
Vpns offer features such as confidentiality,. It enables you to connect your computer or mobile device to a private network, creating an encrypted connection that conceals your ip. When you connect to the internet through a vpn, all your data traffic is sent through an encrypted. 121 VPN Concepts Free CCNA Study Guide.
 Source: supportforums.cisco.com
Source: supportforums.cisco.com
Data is transmitted securely using the ipsec sas. Vpn stands for virtual private network. Vpns can be used as an alternative to private wan connections and offer a secure connection over an insecure medium, such as the internet. SitetoSite VPN between Cisco ASA and Microsoft Azure Virtual Network.
 Source: deltaconfig.com
Source: deltaconfig.com
Dmvpn phase 1 basic configuration. In seven years several things have changed: A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. IP SLA on Cisco Router Cisco Router Link Aggregation Configuring Cisco.

A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Vpn is a technique for segregating traffic from. Dmvpn phase 1 basic configuration. Configuring Cisco 2811 router for Sitetosite VPN with MX Series.
 Source: deltaconfig.com
Source: deltaconfig.com
Group encrypted transport vpn (getvpn) introduces the concept of. This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn Vpn is a technique for segregating traffic from. asaroutervpn Configuring Cisco.
 Source: windward.solutions
Source: windward.solutions
It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct. Group encrypted transport vpn (getvpn) introduces the concept of. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Vpn hairpinning.
 Source: cisco.com
Source: cisco.com
In very simple terms i�m trying to get my head round the order of a vpn. Configure clientless ssl vpn (webvpn) on the asa. This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn Configuration Example of ASA VPN with Overlapping Scenarios Cisco.
 Source: vpnrouterpomil.blogspot.com
Source: vpnrouterpomil.blogspot.com
This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn Vpns offer features such as confidentiality,. We use ipsec and preshared keys, i would. Vpn Router Vpn Configuration On Cisco Router Examples.
 Source: deltaconfig.com
Source: deltaconfig.com
A virtual private network (vpn) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices. A virtual private network (vpn) extends a company�s network, allowing secure remote user access through encrypted connections over the internet. Vpn stands for virtual private network. l2tp on cisco router Configuring Cisco.
 Source: community.fs.com
Source: community.fs.com
Dmvpn phase 1 basic configuration. The encrypted connection helps ensure that sensitive data is safely transmitted. Cisco get vpn members and juniper group vpn members can interoperate as long as the server role is played by a cisco get vpn server, juniper networks security. SD WAN vs MPLS Pros and Cons FS Community.
 Source: aws.amazon.com
Source: aws.amazon.com
The template manager in the vpn solutions center software is a provisioning system that provides fast, flexible, and extensible cisco ios command generation capability. The five steps are summarized as follows: This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn Cisco ASAv Remote Access VPN for AWS with External MultiFactor.

A virtual private network (vpn) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices. A virtual private network (vpn) is an encrypted tunnel between two or more devices, usually a firewall, such as the cisco adaptive security appliance (cisco asa), over an unsecured. Interesting traffic initiates the ipsec process —traffic is deemed interesting when the ipsec security policy configured in the. SitetoSite VPN Configuration Tutorial (Cisco ASA 8.3 , 8.4 and Newer).
 Source: deltaconfig.com
Source: deltaconfig.com
This video is from the cisco simos class at stormwind live, in this section we explore the differences between the newer ssl vpn and legacy ipsec vpn Phase 2 = show crypto ipsec sa. A virtual private network carries private traffic over public network. asaroutervpn Configuring Cisco.

Vpns offer features such as confidentiality,. In an old post, dated 2011, i explained various types of vpn technologies. Cisco get vpn members and juniper group vpn members can interoperate as long as the server role is played by a cisco get vpn server, juniper networks security. What Is Split Tunnel Vpn Cisco WATISVPS.
 Source: cuckoonetworks.blogspot.com
Source: cuckoonetworks.blogspot.com
A virtual private network carries private traffic over public network. How does a vpn work? Dmvpn phase 1 basic configuration. Networking Arena Cuckoo Networks Scenarios and Labs Site to Site.
This Video Is From The Cisco Simos Class At Stormwind Live, In This Section We Explore The Differences Between The Newer Ssl Vpn And Legacy Ipsec Vpn
Dmvpn phase 1 basic configuration. Can some one please explain get vpn to me, the concept of what the key server does and what the group members do is not making any sence and how the group member acually. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Software & tech / by cecil howell / march 22, 2021.
How Does A Vpn Work?
Vpns offer features such as confidentiality,. Vpn means virtual private network. Vpns can be used as an alternative to private wan connections and offer a secure connection over an insecure medium, such as the internet. The encrypted connection helps ensure that sensitive data is safely transmitted.
Data Is Transmitted Securely Using The Ipsec Sas.
Interesting traffic initiates the ipsec process —traffic is deemed interesting when the ipsec security policy configured in the. The encrypted connection helps ensure that sensitive data is safely transmitted. We use ipsec and preshared keys, i would. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network.
Vpn Is A Technique For Segregating Traffic From.
It enables you to connect your computer or mobile device to a private network, creating an encrypted connection that conceals your ip. Phase 1 = show crypto isakmp sa or show crypto ikev1 sa or show crypto ikev2 sa. The extranet vpn business scenario explained in chapter 3,. Configure clientless ssl vpn (webvpn) on the asa.







