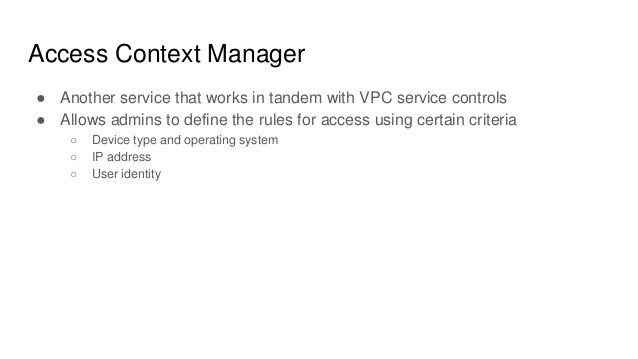
An identity and access management (iam) policy, which specifies access controls for google cloud resources. Let's say i want to give start instance permission ( compute.instances.start) of.
, Just to add to above answer, if during union of the policy, situation of policy conflict occurs then deny takes precedence. Create policy binding member (your friend) with.
 Defcon 27 Exploiting IAM in GCP From slideshare.net
Defcon 27 Exploiting IAM in GCP From slideshare.net
Generates an iam policy document that may be referenced by and applied to other google cloud platform iam resources, such as the gcp.projects.iampolicy. Now consider this resource hierarchy. Iam is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. Can set limits on the roles that a member can grant:
Defcon 27 Exploiting IAM in GCP Iam is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources.
With cloud iam, you manage access control by defining who (identity) has what access (role) for which resource. For example, imagine that both yuri@example.com and tal@example.com have the organization role administrator role (roles/iam.organizationroleadmin). Figure 7 shows an example of an iam policy: Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios.
 Source: docs-gcp.qubole.com
Source: docs-gcp.qubole.com
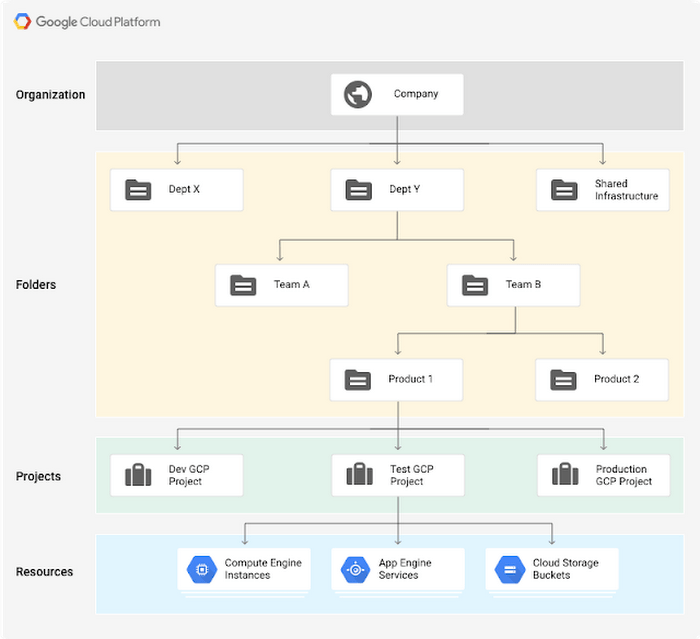
Now consider this resource hierarchy. Not only that but how google uses projects to segregate different. Just to add to above answer, if during union of the policy, situation of policy conflict occurs then deny takes precedence. Automated Setup — Qubole Data Service documentation.

A policy that allows identities from the pool to impersonate the service account. You assign (or bind) a role to a member; For example there are below two policies. GCP Cloud IAM hypemarc 하이프마크.
 Source: youtube.com
Source: youtube.com
For example, imagine that both yuri@example.com and tal@example.com have the organization role administrator role (roles/iam.organizationroleadmin). Now consider this resource hierarchy. Iam is a framework of policies and processes defined by the cloud provider to make sure users have appropriate permissions to access resources, applications and data on. GCP�s Cloud IAM to disable GCE instances Start, Stop & Delete.
 Source: engineering.creditkarma.com
Source: engineering.creditkarma.com
Generates an iam policy document that may be referenced by and applied to other google cloud platform iam resources, such as the gcp.projects.iampolicy. Principals can be user accounts, service. Iam policy for service account. Getting Started with GCP Identity Management Credit Karma Engineering.
 Source: slideshare.net
Source: slideshare.net
Principals can be user accounts, service. Can set limits on the roles that a member can grant: An identity and access management (iam) policy, which specifies access controls for google cloud resources. Defcon 27 Exploiting IAM in GCP.
 Source: testpreptraining.com
Source: testpreptraining.com
When managing iam roles, you can treat a service account either as a resource or as an identity. One thing i love in gcp is how easy it is to manage their iam (identity and access management). Iam is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. Cloud IAM working Google Professional Data Engineer GCP Testprep.
 Source: slideshare.net
Source: slideshare.net
Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios. Iam policy for service account. Gcp is an evolving platform, that constantly adds, and updates features, for example, check out the preview of the deny policy feature. Defcon 27 Exploiting IAM in GCP.
 Source: devsamurai.com
Source: devsamurai.com
Can set limits on the roles that a member can grant: When managing iam roles, you can treat a service account either as a resource or as an identity. Gcp is an evolving platform, that constantly adds, and updates features, for example, check out the preview of the deny policy feature. GCPのサービスを利用権限設定 DevSamurai.
 Source: slideshare.net
Source: slideshare.net
Create policy binding member (your friend) with. Iam policy is an example of that. A policy is a collection of bindings. Defcon 27 Exploiting IAM in GCP.
Three different resources help you manage your iam policy for a service account. Authenticate workloads to the sts endpoint, impersonate the service account, and have them call the. For example, imagine that both yuri@example.com and tal@example.com have the organization role administrator role (roles/iam.organizationroleadmin). Getting to know Cloud IAM Google Cloud Blog.
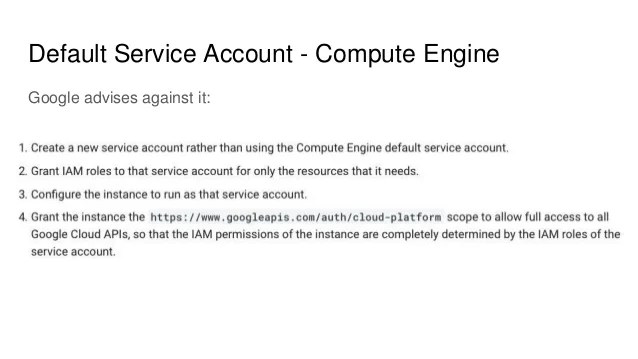 Source: slideshare.net
Source: slideshare.net
With cloud iam, you manage access control by defining who (identity) has what access (role) for which resource. For example, imagine that both yuri@example.com and tal@example.com have the organization role administrator role (roles/iam.organizationroleadmin). To learn which resources support conditions in their iam policies, see the iam documentation. Defcon 27 Exploiting IAM in GCP.
 Source: cloud.google.com
Source: cloud.google.com
A policy that allows identities from the pool to impersonate the service account. Iam is a framework of policies and technologies to ensure that the right users have the appropriate access to technology resources. To learn which resources support conditions in their iam policies, see the iam documentation. Get more control over your Compute Engine resources with new Cloud IAM.
 Source: turtledesk.com
Source: turtledesk.com
Not only that but how google uses projects to segregate different. Choose a role with right permissions (ex: Iam is a framework of policies and processes defined by the cloud provider to make sure users have appropriate permissions to access resources, applications and data on. GCP Essential Series 02.
 Source: blog.nhat-tong.com
Source: blog.nhat-tong.com
Choose a role with right permissions (ex: You assign (or bind) a role to a member; Each of these resources serves a different use case: GCPIAM (Identity and Access Management) Home.
 Source: stackoverflow.com
Source: stackoverflow.com
Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios. Let you create limited iam admins who can manage their own team�s iam policies, but only within the boundaries. Figure 7 shows an example of an iam policy: google cloud platform Make GCP Function Public IAM policy update.
 Source: akku.work
Source: akku.work
Choose a role with right permissions (ex: Figure 7 shows an example of an iam policy: One thing i love in gcp is how easy it is to manage their iam (identity and access management). Meet GCP IAM The Identity and Access Management Solution from Google.
 Source: dev.to
Source: dev.to
You assign (or bind) a role to a member; Each of these resources serves a different use case: Choose a role with right permissions (ex: Identity and Access Management in Cloud DEV Community.
 Source: medium.com
Source: medium.com
To configure permissions for a service account on other. Gcp iam uses the principle of least privilege. A policy that allows identities from the pool to impersonate the service account. Vault auth and secrets on GCP. Sample workflow covering basic use of.
 Source: youtube.com
Source: youtube.com
One thing i love in gcp is how easy it is to manage their iam (identity and access management). Gcp iam uses the principle of least privilege. The set_iam_policy takes as argument a ressource string (exemple projects/myprojectid but i can�t pass the policy to this object, there is not fields for that. ACE1, GCP Associate Cloud Engineer Principle of Least Privilege.
 Source: medium.com
Source: medium.com
Iam policy for service account. A policy is a collection of bindings. Four different resources help you manage your iam policy for a project. Structure and Taxonomy of GCP Krishank Dwivedi Medium.
 Source: medium.com
Source: medium.com
One thing i love in gcp is how easy it is to manage their iam (identity and access management). Now consider this resource hierarchy. Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios. Structure and Taxonomy of GCP Krishank Dwivedi Medium.
 Source: blog.nhat-tong.com
Source: blog.nhat-tong.com
Iam is a framework of policies and processes defined by the cloud provider to make sure users have appropriate permissions to access resources, applications and data on. The set_iam_policy takes as argument a ressource string (exemple projects/myprojectid but i can�t pass the policy to this object, there is not fields for that. Now consider this resource hierarchy. GCPIAM (Identity and Access Management) Home.
 Source: slideshare.net
Source: slideshare.net
Let�s say i want to give start instance permission ( compute.instances.start) of. When managing iam roles, you can treat a service account either as a resource or as an identity. Four different resources help you manage your iam policy for a project. Defcon 27 Exploiting IAM in GCP.
 Source: cloudsteak.com
Source: cloudsteak.com
Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios. Gcp is an evolving platform, that constantly adds, and updates features, for example, check out the preview of the deny policy feature. Choose a role with right permissions (ex: GCP Managing cloud firewalls at scale with new Hierarchical Firewall.
 Source: ameblo.jp
Source: ameblo.jp
With iam conditions, you can choose to grant. Gcp iam uses the principle of least privilege. Iam is a framework of policies and processes defined by the cloud provider to make sure users have appropriate permissions to access resources, applications and data on. GCPのCloud IAMを試してみた サイバーエージェント 公式エンジニアブログ.
Gcp Iam Uses The Principle Of Least Privilege.
Now consider this resource hierarchy. Principals can be user accounts, service. A binding binds one or more members, or principals, to a single role. One thing i love in gcp is how easy it is to manage their iam (identity and access management).
Figure 7 Shows An Example Of An Iam Policy:
A policy that allows identities from the pool to impersonate the service account. With cloud iam, you manage access control by defining who (identity) has what access (role) for which resource. Generates an iam policy document that may be referenced by and applied to other google cloud platform iam resources, such as the gcp.projects.iampolicy. Choose a role with right permissions (ex:
Let�s Say I Want To Give Start Instance Permission ( Compute.instances.start) Of.
Can set limits on the roles that a member can grant: An identity and access management (iam) policy, which specifies access controls for google cloud resources. Assess, plan, implement, and measure software practices and capabilities to modernize and simplify your organization’s business application portfolios. Four different resources help you manage your iam policy for a project.
Authenticate Workloads To The Sts Endpoint, Impersonate The Service Account, And Have Them Call The.
For example, compute engine virtual machine instances,. A policy is a collection of bindings. You assign (or bind) a role to a member; Three different resources help you manage your iam policy for a service account.







