Use cases for firepower threat defense; User groups are created on the router for a collection of users that share the same set of services.
, User groups are created on the router for a collection of users that share the same set of services. This gives the user access to all ip based applications.
 IPSec VPN Knowledge base Selectel From kb.selectel.com
IPSec VPN Knowledge base Selectel From kb.selectel.com
The cisco live presentations such as brksec. For globalprotect ipsec, i�d like to switch from. Internally there used to be the rtr (route to readiness) guides, i think they used to cover vpns, you may want to check there. Interesting traffic initiates the ipsec.
IPSec VPN Knowledge base Selectel Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn.
It could be based on cisco’s dynamic multipoint vpn (dmvpn) technology; The cisco live presentations such as brksec. Much of today’s workforce (approximately 40. Use cases for firepower threat defense;
 Source: docs.oracle.com
Source: docs.oracle.com
The cisco live presentations such as brksec. This gives the user access to all ip based applications. Interesting traffic initiates the ipsec. Cisco ASA RouteBased.
 Source: bestvpnretsuhito.blogspot.com
This article provides some fortinet recommendations for best practices when setting up ipsec vpn environments. Ipsec involves many component technologies and encryption methods. Ipsec vpn is a standard protocol that allows a variety of solutions for endpoint connectivity, including forticlient. Best Vpn Cisco Vpn Best Practices.
 Source: bestvpnhidzuriho.blogspot.com
Source: bestvpnhidzuriho.blogspot.com
The vpn gateway is located at the perimeter of the. This could be a corporate network where multiple offices work in conjunction with. Interesting traffic initiates the ipsec. Best Vpn Cisco Site To Site Vpn Best Practices.
 Source: slideshare.net
Source: slideshare.net
This article provides some fortinet recommendations for best practices when setting up ipsec vpn environments. Internet protocol security (ipsec) is a network layer security control used to protect. The national security agency (nsa) has published a series of recommendations on how to properly configure ip security (ipsec) virtual private networks (vpns). Best practices for using VPNs for easy protection.
 Source: kb.selectel.com
Source: kb.selectel.com
Here are some of the highlights from the recommendations: Vpns that use accepted standards, such as internet key exchange/internet. Use cases for firepower threat defense; L2TP over IPsec Knowledge base Selectel.
 Source: docs.vmware.com
Source: docs.vmware.com
Here are some of the highlights from the recommendations: This could be a corporate network where multiple offices work in conjunction with. Interesting traffic initiates the ipsec. L2 VPN Overview.
 Source: searchenterprisewan.techtarget.com
Source: searchenterprisewan.techtarget.com
It could be based on cisco’s dynamic multipoint vpn (dmvpn) technology; Vpns that use accepted standards, such as internet key exchange/internet. This could be a corporate network where multiple offices work in conjunction with. VPN types Protocols and network topologies of IPsec VPNs.
 Source: bestvpnretsuhito.blogspot.com
Source: bestvpnretsuhito.blogspot.com
The national security agency (nsa) has published a series of recommendations on how to properly configure ip security (ipsec) virtual private networks (vpns). Frankel, karen scarfone, paul wouters. Here are some of the highlights from the recommendations: Best Vpn Cisco Vpn Best Practices.
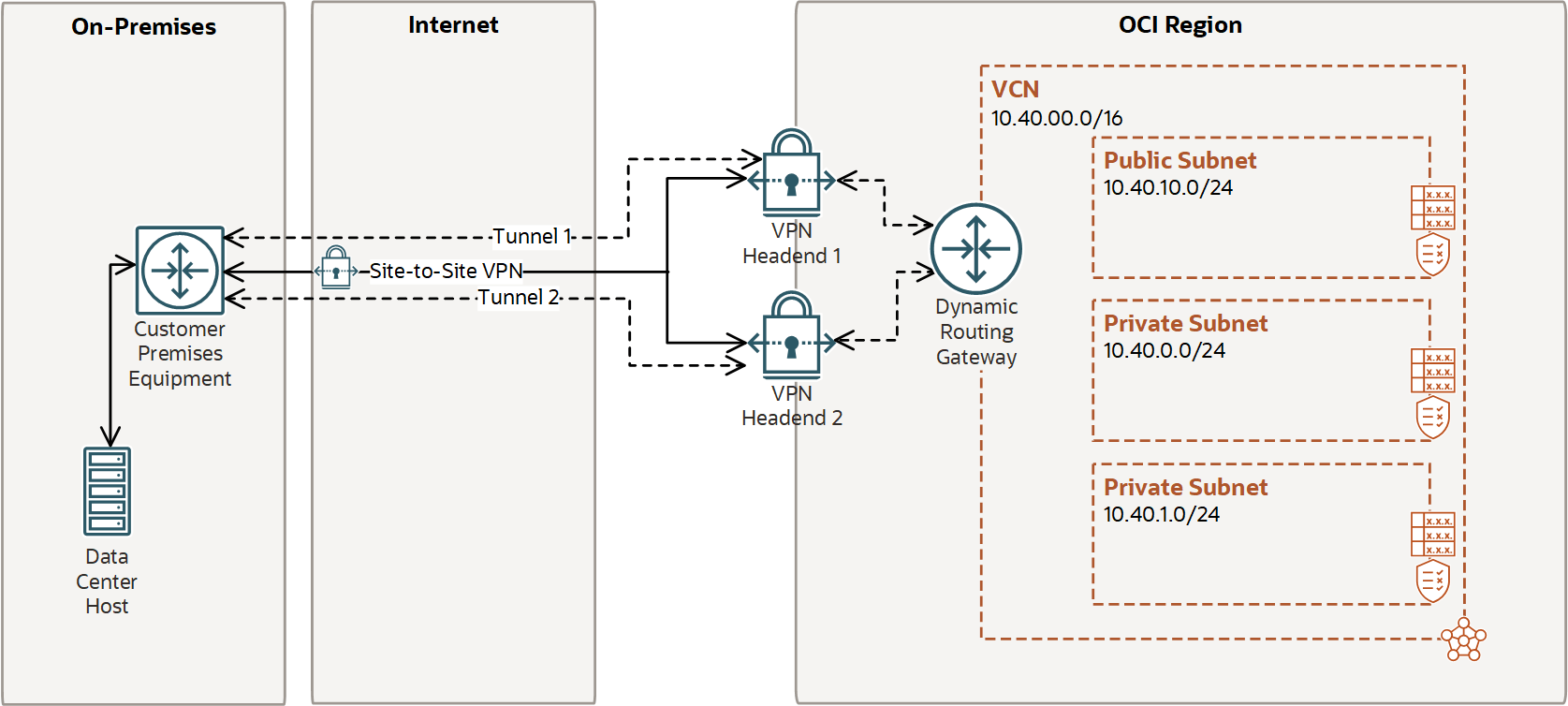 Source: docs.cloud.oracle.com
Source: docs.cloud.oracle.com
Frankel, karen scarfone, paul wouters. It is a well defined protocol that uses specific ports, and it is not. This gives the user access to all ip based applications. Libreswan.
 Source: bestvpnretsuhito.blogspot.com
Source: bestvpnretsuhito.blogspot.com
These user groups include options for the group, like a list of permissions on. This could be a corporate network where multiple offices work in conjunction with. Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn. Best Vpn Cisco Vpn Best Practices.
 Source: cisco.com
Source: cisco.com
Ipsec tunnel parameter best practices. Set up an ipsec tunnel; As with most technical configurations, every managed service provider should follow a set of best practices while managing virtual private networks. Voice and Video Enabled IPSec VPN (V3PN) Solution Reference Network.
![[SOLVED] any best practices on IPSec SitetoSite not being as the edge [SOLVED] any best practices on IPSec SitetoSite not being as the edge](https://i2.wp.com/content.spiceworksstatic.com/service.community/p/post_attachments/0000152515/528716a9/attached_file/SC.jpg) Source: community.spiceworks.com
Source: community.spiceworks.com
Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn. The national security agency (nsa) has published a series of recommendations on how to properly configure ip security (ipsec) virtual private networks (vpns). The vpn gateway is located at the perimeter of the. [SOLVED] any best practices on IPSec SitetoSite not being as the edge.
 Source: lira.epac.to
The vpn gateway is located at the perimeter of the. This could be a corporate network where multiple offices work in conjunction with. Ipsec involves many component technologies and encryption methods. ch15lev1sec4.html.
 Source: flylib.com
Source: flylib.com
This article provides some fortinet recommendations for best practices when setting up ipsec vpn environments. The vpn gateway is located at the perimeter of the. Set up an ipsec tunnel; SitetoSite Deployment Examples IPsec VPN Design Considerations.
 Source: docs.oracle.com
Source: docs.oracle.com
It is a well defined protocol that uses specific ports, and it is not. The vpn gateway is located at the perimeter of the. (1) do not setup a vpn ipsec. Cisco ASA RouteBased.
 Source: cisco.com
Source: cisco.com
Internally there used to be the rtr (route to readiness) guides, i think they used to cover vpns, you may want to check there. Frankel, karen scarfone, paul wouters. This could be a corporate network where multiple offices work in conjunction with. Voice and Video Enabled IPSec VPN (V3PN) Solution Reference Network.
 Source: indeni.com
Source: indeni.com
Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn. Cradlepoint devices allow an ipsec psk of up to 128 characters, but this may vary with different vendors, so make sure your psk length is supported by all routers. This article provides some fortinet recommendations for best practices when setting up ipsec vpn environments. Palo Alto IPSec VPN Config How to Set Up Between PAN & Cisco ASA Indeni.

Here are some of the highlights from the recommendations: It could be based on cisco’s dynamic multipoint vpn (dmvpn) technology; Use cases for firepower threat defense; Best Practices Configure IPSec VPN template via NetCloud Manager (NCM.
 Source: kb.selectel.com
Source: kb.selectel.com
Set up an ipsec tunnel; (1) do not setup a vpn ipsec. An ipsec vpn could be a standard ipsec vpn; IPSec VPN Knowledge base Selectel.
 Source: myshared.ru
Source: myshared.ru
If necessary, you can have fortigate. Set up an ipsec tunnel; User groups are created on the router for a collection of users that share the same set of services. Презентация на тему "© 2006 Cisco Systems, Inc. All rights reserved.

This could be a corporate network where multiple offices work in conjunction with. I read from (juniper� site or juniper blogs or something) that for example in phase. Ipsec is used to connect a remote user to an entire network. CloudHub VPC IPsec VPN Monitoring and Troubleshooting Guide MuleSoft.
 Source: bestvpnhidzuriho.blogspot.com
Source: bestvpnhidzuriho.blogspot.com
Internally there used to be the rtr (route to readiness) guides, i think they used to cover vpns, you may want to check there. As with most technical configurations, every managed service provider should follow a set of best practices while managing virtual private networks. Here are some of the highlights from the recommendations: Best Vpn Site To Site Vpn Best Practices.
 Source: bestvpnretsuhito.blogspot.com
Source: bestvpnretsuhito.blogspot.com
For globalprotect ipsec, i�d like to switch from. Ipsec tunnel parameter best practices. Yet ipsec�s operation can be broken down into five main steps: Best Vpn Vpn Implementation Best Practices.
 Source: myshared.ru
Source: myshared.ru
Frankel, karen scarfone, paul wouters. Set up an ipsec tunnel; If necessary, you can have fortigate. Презентация на тему "© 2006 Cisco Systems, Inc. All rights reserved.
 Source: community.sophos.com
Source: community.sophos.com
Use cases for firepower threat defense; This gives the user access to all ip based applications. Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn. Best practice for sitetosite policybased IPsec VPN.
Cradlepoint Devices Allow An Ipsec Psk Of Up To 128 Characters, But This May Vary With Different Vendors, So Make Sure Your Psk Length Is Supported By All Routers.
Finally, you are presented with a collection of cisco best practices for configuring an ipsec vpn. Much of today’s workforce (approximately 40. This article provides some fortinet recommendations for best practices when setting up ipsec vpn environments. As with most technical configurations, every managed service provider should follow a set of best practices while managing virtual private networks.
I Read From (Juniper� Site Or Juniper Blogs Or Something) That For Example In Phase.
It is a well defined protocol that uses specific ports, and it is not. For globalprotect ipsec, i�d like to switch from. Yet ipsec�s operation can be broken down into five main steps: Here are some of the highlights from the recommendations:
An Ipsec Vpn Could Be A Standard Ipsec Vpn;
The vpn gateway is located at the perimeter of the. The cisco live presentations such as brksec. Vpns that use accepted standards, such as internet key exchange/internet. Internet protocol security (ipsec) is a network layer security control used to protect.
Set Up An Ipsec Tunnel;
Ipsec is used to connect a remote user to an entire network. The national security agency (nsa) has published a series of recommendations on how to properly configure ip security (ipsec) virtual private networks (vpns). These user groups include options for the group, like a list of permissions on. Interesting traffic initiates the ipsec.







