If you’re looking to set up your firewall to allow an ipsec vpn connection, be sure to open udp port 500 and ip ports 50 and 51. Ike is a key management and authentication mechanism used by ipsec vpn.
, Ipsec uses the following protocols to perform various functions: Ike is a key management and authentication mechanism used by ipsec vpn.
 IPsec Protocol Security explained CCNA TUTORIALS From ccnatutorials.in
IPsec Protocol Security explained CCNA TUTORIALS From ccnatutorials.in
Software on user or server systems does not need to be changed when ipsec is implemented in the. It guards the overall data packet produced at the ip layer inclusive of the higher layer headers. (a) layer 1 (b) layer 2 (c) layer 3 (d) layer 4. The authentication header protocol provides features like authentication, integrity, and.
IPsec Protocol Security explained CCNA TUTORIALS This means ipsec wraps the original packet,.
This protocol provides authentication services to ipsec. A note on ipsec ports: Ipsec works at the network layer and directly runs over the internet protocol (ip). Ipsec (internet protocol security) is a large set of protocols and algorithms.
 Source: pinterest.com
Source: pinterest.com
The three main protocols comprising ipsec are: As andy lemke mentioned, ipsec suite comprises of. To my understanding mpls is an routing protocol. The TCP/IP Guide IPSec Encapsulating Security Payload (ESP) Cisco.
 Source: tcpipguide.com
Source: tcpipguide.com
The internet engineering task force, or. However, keep in mind that ipsec has two modes of implementation in. Ip sec (internet protocol security) is a suite of protocols and algorithms for securing data transmitted over the internet or any public network. The TCP/IP Guide IPSec Architectures and Implementation Methods.
 Source: oditeksolutions.com
Source: oditeksolutions.com
Ipsec is a suite of protocols that provide security services at ip layer of tcp/ip stack i.e. They work on the session layer. This means ipsec wraps the original packet,. Networking, IPSec Development & Testing Services in India OdiTek.
 Source: thesecuritybuddy.com
Source: thesecuritybuddy.com
Unlike ipsec, which works on the ip layer, tls works on the transport layer. The authentication header protocol provides features like authentication, integrity, and. They function on either the application or the physical. What is IPSec protocol and how does it work.
 Source: techmindug.blogspot.com
Source: techmindug.blogspot.com
Ipsec layer lies in between the transport layer and the internet layer. With ipsec vpn, your traffic is. Ip sec (internet protocol security) is a suite of protocols and algorithms for securing data transmitted over the internet or any public network. Understanding VPN IPSec Tunnel Mode and IPSec Transport Mode What�s.
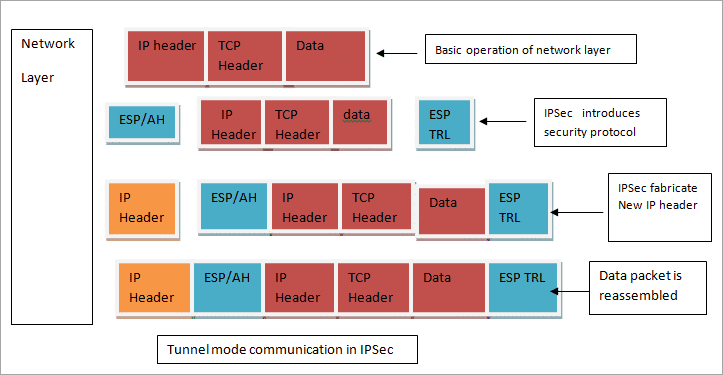 Source: softwaretestinghelp.com
Source: softwaretestinghelp.com
Software on user or server systems does not need to be changed when ipsec is implemented in the. The recipient of the message can verify the authenticity of the sender. Ipsec is transparent to applications because it is above the transport layer. What is IP Security (IPSec), TACACS and AAA Security Protocols.
 Source: slideserve.com
Source: slideserve.com
Ip sec (internet protocol security) is a suite of protocols and algorithms for securing data transmitted over the internet or any public network. They work on the session layer. Let’s take a closer look at what. PPT IPSec (Security at the IP Layer) PowerPoint Presentation, free.
 Source: present5.com
Source: present5.com
Unlike ipsec, which works on the ip layer, tls works on the transport layer. The internet engineering task force, or. Which layer of the osi. Digital Certificates X 509 Open PGP Security Protocols.
 Source: tcpipguide.com
Source: tcpipguide.com
A note on ipsec ports: However, keep in mind that ipsec has two modes of implementation in. They work on the session layer. The TCP/IP Guide IPSec Modes Transport and Tunnel.
 Source: academlib.com
Source: academlib.com
Ipsec is transparent to applications because it is above the transport layer. But there’s just one more thing: (a) layer 1 (b) layer 2 (c) layer 3 (d) layer 4. Layer Two Tunneling Protocol (L2TPv3), Protocol Security.
 Source: slideserve.com
Source: slideserve.com
The three main protocols comprising ipsec are: Start your free software development course. Ipsec uses the following protocols to perform various functions: PPT Lecture 13 PowerPoint Presentation, free download ID1227561.
 Source: wallpaperrustic.blogspot.com
The internet engineering task force, or. Ipsec (internet protocol security) is a large set of protocols and algorithms. With ipsec vpn, your traffic is. Ipsec Ipsec is a protocol suite for encrypting network communications.
 Source: slideserve.com
Source: slideserve.com
She will most likely be implementing ipsec vpn tunnels to connect the offices. A note on ipsec ports: To my understanding mpls is an routing protocol. PPT Network Security IPsec PowerPoint Presentation ID5686700.

The recipient of the message can verify the authenticity of the sender. Network layer in osi model. However, keep in mind that ipsec has two modes of implementation in. Figure 5.1 Two ways of implementing IPSec; integrated and "bumpinthe.
 Source: slideserve.com
Source: slideserve.com
Which layer of the osi. Ip sec (internet protocol security) is a suite of protocols and algorithms for securing data transmitted over the internet or any public network. They function on either the application or the physical. PPT IPSec (Security at the IP Layer) PowerPoint Presentation, free.
 Source: crashtest-security.com
Source: crashtest-security.com
Ipsec is majorly used for securing data transmitted all over the internet. Here is a list of protocols that ipsec is using during the transmission of the data. A note on ipsec ports: What is TLS, SSL, HTTP, and HTTPS? And how do they work together.
 Source: researchgate.net
Source: researchgate.net
Ipsec is a suite of protocols that provide security services at ip layer of tcp/ip stack i.e. The internet engineering task force, or. Ipsec uses the following protocols to perform various functions: The IPSec Architecture Download Scientific Diagram.
 Source: ccnatutorials.in
Source: ccnatutorials.in
Ipsec layer lies in between the transport layer and the internet layer. Rated by 1 million+ students. Ipsec is a suite of protocols that provide security services at ip layer of tcp/ip stack i.e. IPsec Protocol Security explained CCNA TUTORIALS.
 Source: researchgate.net
Source: researchgate.net
Ipsec is a suite of protocols widely used to secure connections over the internet. Ipsec tunnel mode is the default mode. We negotiate a security association to build the ike phase 1 tunnel (isakmp tunnel). A logical structure of the IPsec security module. Download Scientific.
 Source: computersecuritypgp.blogspot.com
Source: computersecuritypgp.blogspot.com
Which layer of the osi. The internet engineering task force, or. Ipsec is transparent to applications because it is above the transport layer. Computer Security and PGP What Is IP Security or IPSec Protocol?.
 Source: academlib.com
Source: academlib.com
With tunnel mode, the entire original ip packet is protected by ipsec. But there’s just one more thing: It guards the overall data packet produced at the ip layer inclusive of the higher layer headers. Layer Two Tunneling Protocol (L2TPv3), Protocol Security.
 Source: slideshare.net
Source: slideshare.net
Ipsec is transparent to applications because it is above the transport layer. The internet engineering task force, or. She will most likely be implementing ipsec vpn tunnels to connect the offices. IPSec and VPN.
 Source: slideserve.com
Source: slideserve.com
Here is a list of protocols that ipsec is using during the transmission of the data. Ipsec uses the following protocols to perform various functions: But there’s just one more thing: PPT IPsec Network Layer Security PowerPoint Presentation, free.
 Source: researchgate.net
Source: researchgate.net
Ipsec is a suite of protocols widely used to secure connections over the internet. Start your free software development course. This means ipsec wraps the original packet,. 2 The securityrelated protocols associated with the TCP/IP protocol.
 Source: dailycybersecurity.blogspot.com
Source: dailycybersecurity.blogspot.com
With ipsec vpn, your traffic is. Within the ike phase 1 tunnel, we build the ike phase 2 tunnel (ipsec tunnel). It guards the overall data packet produced at the ip layer inclusive of the higher layer headers. Harshani Somarathne IPsec Protocol.
This Protocol Provides Authentication Services To Ipsec.
Ipsec is a suite of protocols widely used to secure connections over the internet. Let’s take a closer look at what. Network layer in osi model. The recipient of the message can verify the authenticity of the sender.
Ipsec Works At The Network Layer And Directly Runs Over The Internet Protocol (Ip).
Web development, programming languages, software testing & others. The three main protocols comprising ipsec are: They work on the session layer. It guards the overall data packet produced at the ip layer inclusive of the higher layer headers.
Rated By 1 Million+ Students.
Ipsec is a suite of protocols that provide security services at ip layer of tcp/ip stack i.e. Software on user or server systems does not need to be changed when ipsec is implemented in the. The ipsec is an open standard as a part of the ipv4 suite. Ike is a key management and authentication mechanism used by ipsec vpn.
As Andy Lemke Mentioned, Ipsec Suite Comprises Of.
Start your free software development course. It goes a bit deeper than that, but these are the basics of how ipsec works. Which layer of the osi. The authentication header protocol provides features like authentication, integrity, and.







