Rls best practices for data sources and workbooks. Of course, postgresql offers many advanced security.
, In the above diagram users are authorised to view data for one or more. Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations.
 Row Level Security Azure SQL Server Security (Part 1 From visualbi.com
Row Level Security Azure SQL Server Security (Part 1 From visualbi.com
It can be an additional layer of security when an application is. The following few steps demonstrate the technique. This article targets you as a data modeler working with power bi desktop. Create the tabular model with facts and dimension tables.
Row Level Security Azure SQL Server Security (Part 1 Row level security best practice.
Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. Create the tabular model with facts and dimension tables. Row level security is a highly flexible technique for controlling which records are returned based on the current user. Rls best practices for data sources and workbooks.
 Source: softelligence.net
Source: softelligence.net
Rls best practices for data sources and workbooks. Row level security is a highly flexible technique for controlling which records are returned based on the current user. Create the tabular model with facts and dimension tables. Governance in Analytics Part 1 SelfService.
 Source: visualbi.com
Source: visualbi.com
Of course, postgresql offers many advanced security. Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations. First introduced in azure sql, in january. Row Level Security Azure SQL Server Security (Part 1.
 Source: snp.com
Source: snp.com
Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations. The security best practices mentioned above will help you protect your data and your business’s reputation. Filters restrict data access at the row level, and you can define filters within role. Bring your Data Securely to the Cloud by Implementing Column Level.

I am writing this question to seek some answer on row level security implementation. It can be an additional layer of security when an application is. Row level security allows to implement the differentiation of access rights to data using the database tools. Ranjeet Vidwans on LinkedIn TrustLogix Integrates with AWS Redshift.
 Source: visualbi.com
Source: visualbi.com
Create the user security table and define data relationship. The security best practices mentioned above will help you protect your data and your business’s reputation. Row assignments in a lookup. Row Level Security Azure SQL Server Security (Part 1.
 Source: slideshare.net
Source: slideshare.net
Row assignments in a lookup. It can be an additional layer of security when an application is. Row level security allows to implement the differentiation of access rights to data using the database tools. Implementing Onboarding Best Practices in Your PeopleSoft HCM.
 Source: sql.info
Source: sql.info
Starting out, i put the dataset/report and the dataflow. Create the user security table and define data relationship. However, it is quite necessary to protect sensitive power bi data and one of the best practices to do so is by implementing power bi row level security (rls). Understanding Google BigQuery Columnar Storage Architecture.
 Source: quest.com
Source: quest.com
Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations. Filters restrict data access at the row level, and you can define filters within role. Create the tabular model with facts and dimension tables. Microsoft Teams Security for IT Admins and Team Owners Microsoft.
 Source: blogs.perficient.com
Source: blogs.perficient.com
Dear gurus, i�m a really beginer in jasper report and we are using v6.0.1 we have a datawarehouse on which we have to do both dashboards/reports and adhoc views. However, it is quite necessary to protect sensitive power bi data and one of the best practices to do so is by implementing power bi row level security (rls). Sometimes, settings can be done with an and filter: Azure SQL Row Level Security Now Available Perficient Blogs.
![Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers](https://fansurf.github.io/img/placeholder.svg)
Hello cummunity, i hope all are doing well during this tough time. In the above diagram users are authorised to view data for one or more. There is no option to override this setting;. Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers.
 Source: criticaleg.com
Source: criticaleg.com
It can be an additional layer of security when an application is. The following few steps demonstrate the technique. A few days ago i’ve blogged about the common issues with roles and privileges we discover during security reviews. CEG VlogLesser Known Airflow Management Best Practices.
 Source: smartbridge.com
Source: smartbridge.com
Furthermore, this is done transparently for applications interacting with the. By default, dynamodb enables encryption at rest for all tables. Create the user security table and define data relationship. JDE Security Best Practices (Part II) Business Unit Security.
 Source: sqlservercentral.com
Source: sqlservercentral.com
This article targets you as a data modeler working with power bi desktop. Row assignments in a lookup. Hello cummunity, i hope all are doing well during this tough time. RowLevel Security Predicate Functions Level 2 of the Stairway to Row.
 Source: help.tableau.com
Source: help.tableau.com
Best practices for preventive security. The security best practices mentioned above will help you protect your data and your business’s reputation. Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. Restrict Data Access with User Filters and Row Level Security Tableau.
 Source: visualbi.com
Source: visualbi.com
Dear gurus, i�m a really beginer in jasper report and we are using v6.0.1 we have a datawarehouse on which we have to do both dashboards/reports and adhoc views. Row level security allows to implement the differentiation of access rights to data using the database tools. Row level security is a highly flexible technique for controlling which records are returned based on the current user. Row Level Security Azure SQL Server Security (Part 2.
 Source: visualbi.com
Source: visualbi.com
Row assignments in a lookup. There is no option to override this setting;. It can be an additional layer of security when an application is. Row Level Security Azure SQL Server Security (Part 1.
 Source: visualbi.com
Source: visualbi.com
Of course, postgresql offers many advanced security. Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations. Dear gurus, i�m a really beginer in jasper report and we are using v6.0.1 we have a datawarehouse on which we have to do both dashboards/reports and adhoc views. Row Level Security Azure SQL Server Security (Part 1.
 Source: theinformationlab.nl
Source: theinformationlab.nl
Best practices for preventive security. Create the user security table and define data relationship. The following few steps demonstrate the technique. Tableau Conference Sessions 2020 The top 5 session you cannot miss.
 Source: stealthbits.com
Source: stealthbits.com
Best practices for preventive security. There is no option to override this setting;. Row level security with power bi can be used to restrict data access for given users. Database Security Best Practices Simple & Worthwhile Concepts Part.
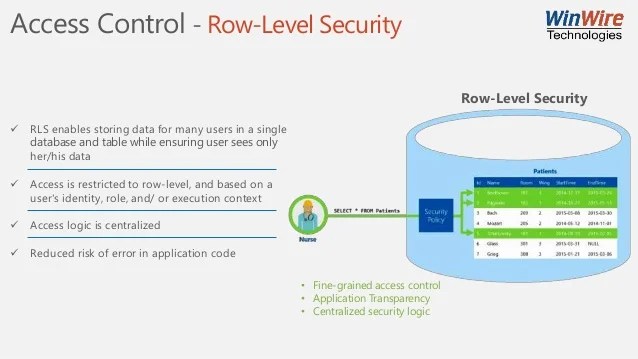 Source: fr.slideshare.net
Source: fr.slideshare.net
This article targets you as a data modeler working with power bi desktop. Presentation content overview setting up rls filter predicates blocking predicates best practices considerations and limitations. Starting out, i put the dataset/report and the dataflow. Modern Data Security for the Enterprises SQL Server & Azure SQL Dat….
 Source: knowledgehut.com
Source: knowledgehut.com
Row level security is a highly flexible technique for controlling which records are returned based on the current user. There is no option to override this setting;. A few days ago i’ve blogged about the common issues with roles and privileges we discover during security reviews. What are the Power BI best practices for Designing & Reporting?.
 Source: medium.com
Source: medium.com
Create the user security table and define data relationship. Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. Row level security best practice. EA Certification Study Guide Part 5 Security by Kelsey Shannon Medium.
![Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers](https://i2.wp.com/jealouscomputers.com/wp-content/uploads/2021/01/Data-Warehouse-Security-Best-Practices-Snowflake-1024x472.png) Source: jealouscomputers.com
Source: jealouscomputers.com
A few days ago i’ve blogged about the common issues with roles and privileges we discover during security reviews. Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. Dear gurus, i�m a really beginer in jasper report and we are using v6.0.1 we have a datawarehouse on which we have to do both dashboards/reports and adhoc views. Data Warehouse Security Best Practices [Snowflake] 🖥️ Jealous Computers.
 Source: visualbi.com
Source: visualbi.com
Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. Of course, postgresql offers many advanced security. Row level security best practice. Row Level Security Azure SQL Server Security (Part 1.
 Source: spreadsheeto.com
Source: spreadsheeto.com
Of course, postgresql offers many advanced security. Sometimes, settings can be done with an and filter: Row level security allows to implement the differentiation of access rights to data using the database tools. Power BI Best Practices 10 Guidelines to Always Follow.
Furthermore, This Is Done Transparently For Applications Interacting With The.
Row level security best practice. Of course, postgresql offers many advanced security. Row level security with power bi can be used to restrict data access for given users. Rows assigned directly to users.
Row Level Security Is A Highly Flexible Technique For Controlling Which Records Are Returned Based On The Current User.
Create the tabular model with facts and dimension tables. A few days ago i’ve blogged about the common issues with roles and privileges we discover during security reviews. Row assignments in a lookup. Best practices for preventive security.
Row Level Security Allows To Implement The Differentiation Of Access Rights To Data Using The Database Tools.
It can be an additional layer of security when an application is. By default, dynamodb enables encryption at rest for all tables. The security best practices mentioned above will help you protect your data and your business’s reputation. Dear gurus, i�m a really beginer in jasper report and we are using v6.0.1 we have a datawarehouse on which we have to do both dashboards/reports and adhoc views.
This Article Targets You As A Data Modeler Working With Power Bi Desktop.
Starting out, i put the dataset/report and the dataflow. I am writing this question to seek some answer on row level security implementation. Would like to be able to limit the sales people to only see their own data, regional managers to see their own regional data, and executive level to be able to see all the data. The following few steps demonstrate the technique.







