The first requirement of any good vpn privacy policy is that it actually has to exist. The purpose of this policy is to provide guidelines for remote access virtual private network (vpn) connections to the nc state university network.
, Jurisdiction and logging policies with vpn services. Ip addresses (only for users who choose to use the.
 What is a VPN Block and How to Get Around Them Foreign policy From foreignpolicyi.org
What is a VPN Block and How to Get Around Them Foreign policy From foreignpolicyi.org
The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. These connections provide secure tunnels allowing access to a remote network. The purpose of this policy is to provide guidelines for remote access virtual private network (vpn) connections to the nc state university network. This policy applies to implementations of vpn that are directed through a vpn gateway.
What is a VPN Block and How to Get Around Them Foreign policy 12 rows the policy dictates either some or all of the interesting traffic should traverse via vpn.
Another not insignificant part though is that any vpn provider or isp that does store usage. Aggregate apps and vpn connection summary statistics; Vpn stands for the virtual private network. Use vpn for all process on the router:
 Source: techwibe.com
Source: techwibe.com
The first requirement of any good vpn privacy policy is that it actually has to exist. Jurisdiction is an important factor. A virtual private network (vpn) is a technology that creates a safe and encrypted connection over a less secure network, such as. Trust Zone VPN Follows Strict No Logging Policy Review.
 Source: slideshare.net
Source: slideshare.net
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. The policy comes into effect on june 28, 60 days after the announcement. Learn more about what a remote work policy is and how to create one. Virtual Private Networks (VPN) ppt.
 Source: vpncompare.co.uk
Source: vpncompare.co.uk
A remote work policy is an agreement that describes everything needed to allow employees to work from home. Another not insignificant part though is that any vpn provider or isp that does store usage. Is not allowed is also. 4 out 10 VPN services� logging practices critically unclear VPN Compare.
 Source: thebestvpn.com
Source: thebestvpn.com
Use vpn for guest network: A virtual private network (vpn) is a technology that creates a safe and encrypted connection over a less secure network, such as. The policy comes into effect on june 28, 60 days after the announcement. 100+ VPNs & Their Logging Policy (What Logs Are Kept by Who?).
 Source: thetechninjas.com
Source: thetechninjas.com
Generally, the traffic of all processes. The encrypted connection helps ensure that sensitive data is safely transmitted. This policy applies to implementations of vpn that are directed through a vpn gateway. What is a VPN, and How Does It Work? The Tech Ninjas.
 Source: thebestvpn.com
Source: thebestvpn.com
Jurisdiction is an important factor. If you can’t comprehend what’s amazing about this claim, do take note that pia operates in the us. Use vpn for all process on the router: 100+ VPNs & Their Logging Policy (What Logs Are Kept by Who?).
 Source: gobestvpn.com
Source: gobestvpn.com
This policy compliments the ncss’s remote access policy, as both documents are necessary for implementing a safe remote access policy for your company. Is not allowed is also. Vpn connections are most commonly used for remote staff and vendor support functions. Top 10 VPN Logging Policies & Verified NoLog VPNs (Policy Analysis).
 Source: anonymania.com
Source: anonymania.com
Generally, the traffic of all processes. These connections provide secure tunnels allowing access to a remote network. This policy applies to implementations of vpn that are directed through a vpn gateway. What is a VPN ZeroLogs Policy and Why Is It Important? Anonymania.
![What My ISP Sees When I Use VPN [Explained] The Movie Blog What My ISP Sees When I Use VPN [Explained] The Movie Blog](https://i2.wp.com/www.themovieblog.com/wp-content/uploads/2019/10/best-vpn-china-vpn-computer-service-2063636.jpg) Source: themovieblog.com
Source: themovieblog.com
Internet protocol security (ipsec) profiles specify a set of encryption and authentication settings for an internet key exchange (ike). Is not allowed is also. 12 rows the policy dictates either some or all of the interesting traffic should traverse via vpn. What My ISP Sees When I Use VPN [Explained] The Movie Blog.
 Source: techguruhub.net
Source: techguruhub.net
This policy applies to implementations of vpn that are directed through a vpn gateway. One thing to consider with any vpn service is jurisdiction: The purpose of the virtual private network (vpn) policy is to provide guidelines for remote access ipsec or pptp virtual private network (vpn) connections to the archdiocese of. What Is a Virtual Private Network (VPN) and why you should use it.
 Source: techicy.com
Source: techicy.com
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. A vpn or virtual private network allows a user to browse the internet while protecting their identity including masking their device’s ip address, encrypting their data, and. What Is VPN Protocols And How VPN Works? Techicy.
 Source: tenbestvpns.com
Source: tenbestvpns.com
Vpn connections are most commonly used for remote staff and vendor support functions. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Minimizing the risks on those assets and documenting what is allowed and what. ExpressVPN Review Is it The Fastest VPN on Earth?.
 Source: employeesportal.info
Source: employeesportal.info
The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. Jurisdiction and logging policies with vpn services. You can use profiles when setting. PTA VPN Policy 2020 EmployeesPortal.
 Source: makeuseof.com
Source: makeuseof.com
The policy would then define the responsibility of the security department: Ip addresses (only for users who choose to use the. Internet protocol security (ipsec) profiles specify a set of encryption and authentication settings for an internet key exchange (ike). The 6 Major VPN Protocols Explained.
 Source: blog.xvpn.io
Source: blog.xvpn.io
A vpn or virtual private network allows a user to browse the internet while protecting their identity including masking their device’s ip address, encrypting their data, and. One thing to consider with any vpn service is jurisdiction: Provide end users with detailed instructions for installing the vpn client on their devices. What is XVPN�s No log policy? XVPN Best Free VPN For iOS.
 Source: incpak.com
Source: incpak.com
The policy would then define the responsibility of the security department: If you can’t comprehend what’s amazing about this claim, do take note that pia operates in the us. The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. What Is a VPN? Types and How it works? INCPak.
 Source: thebestvpn.com
Source: thebestvpn.com
The first requirement of any good vpn privacy policy is that it actually has to exist. A vpn or virtual private network allows a user to browse the internet while protecting their identity including masking their device’s ip address, encrypting their data, and. The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. 100+ VPN Logging Policies Debunked (2019).
 Source: vpnranks.com
Source: vpnranks.com
A remote work policy is an agreement that describes everything needed to allow employees to work from home. Must protect your company’s critical technology assets. The first requirement of any good vpn privacy policy is that it actually has to exist. RA4W VPN Review 2019 Is It Worth Your Money?.
 Source: foreignpolicyi.org
Source: foreignpolicyi.org
12 rows the policy dictates either some or all of the interesting traffic should traverse via vpn. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. Approved organization employees and authorized third parties (customers, vendors,. What is a VPN Block and How to Get Around Them Foreign policy.
 Source: ubuntupit.com
Source: ubuntupit.com
Is not allowed is also. If you have heard about the new vpn policy in india and are confused what is it all about, we have. The policy comes into effect on june 28, 60 days after the announcement. How To Set Up A VPN With Linux A Comprehensive Beginner’s Guide.
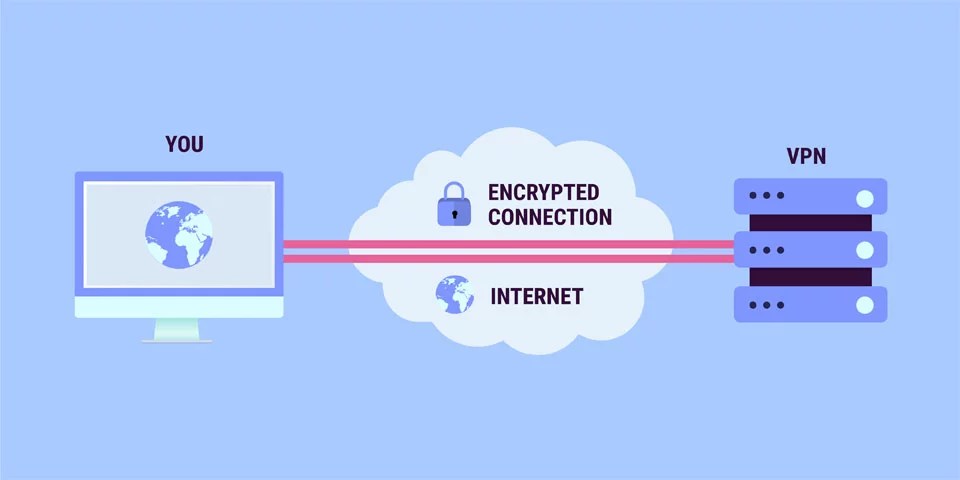 Source: softwaretested.com
Source: softwaretested.com
Provide end users with detailed instructions for installing the vpn client on their devices. But the reality is that many small vpns have privacy policy. If you have heard about the new vpn policy in india and are confused what is it all about, we have. VPNs Are for Security, Not for Saving Money? Here’s How VPN Works.
 Source: help.sonicwall.com
Source: help.sonicwall.com
Is not allowed is also. The encrypted connection helps ensure that sensitive data is safely transmitted. You can use profiles when setting. Creating a WAN GroupVPN.
 Source: ipwithease.com
Source: ipwithease.com
One thing to consider with any vpn service is jurisdiction: These connections provide secure tunnels allowing access to a remote network. Another not insignificant part though is that any vpn provider or isp that does store usage. Policy Based VPN vs Route Based VPN Know the Difference IP With Ease.
 Source: cyberblogindia.in
Source: cyberblogindia.in
12 rows the policy dictates either some or all of the interesting traffic should traverse via vpn. Jurisdiction and logging policies with vpn services. Anonymous vpn connection diagnostics and crash reports; What is a VPN and Why do you need it.
 Source: gobestvpn.com
Source: gobestvpn.com
Vpns protect you from online tracking. The remote openvpn client is configured to use the vpn director policy rules so that all traffic to our 192.168.133.0 subnet goes to our headquarters location using the vpn. Turn on/off use vpn for guest network. Top 10 VPN Logging Policies & Verified NoLog VPNs (Policy Analysis).
Approved Organization Employees And Authorized Third Parties (Customers, Vendors,.
Another not insignificant part though is that any vpn provider or isp that does store usage. Vpns provide employees with secure access to an organization’s internal network and data, from anywhere. Anonymous vpn connection diagnostics and crash reports; Okay, yes, that sounds obvious.
Ip Addresses (Only For Users Who Choose To Use The.
Learn more about what a remote work policy is and how to create one. Jurisdiction is an important factor. A remote work policy is an agreement that describes everything needed to allow employees to work from home. Vpns protect you from online tracking.
Must Protect Your Company’s Critical Technology Assets.
But the reality is that many small vpns have privacy policy. Aggregate apps and vpn connection summary statistics; Internet protocol security (ipsec) profiles specify a set of encryption and authentication settings for an internet key exchange (ike). This policy compliments the ncss’s remote access policy, as both documents are necessary for implementing a safe remote access policy for your company.
If You Have Heard About The New Vpn Policy In India And Are Confused What Is It All About, We Have.
The purpose of the virtual private network (vpn) policy is to provide guidelines for remote access ipsec or pptp virtual private network (vpn) connections to the archdiocese of. The purpose of this policy is to provide guidelines for remote access virtual private network (vpn) connections to the nc state university network. This policy applies to implementations of vpn that are directed through a vpn gateway. Use vpn for all process on the router:






