What authentication types for a vpn can be used? Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec.
, Vpn creates an encrypted connection that is called vpn tunnel, and all internet traffic and communication is passed through this secure tunnel. Security policy authentication and virtual private network.
 Why use twofactor authentication (2FA) or Multifactor (MFA) with your From tmdtechnology.com
Why use twofactor authentication (2FA) or Multifactor (MFA) with your From tmdtechnology.com
Virtual private network (vpn) services fall into four main types: Top 5 password hygiene tips and best practices. Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec. The basic sku does not support ikev2 or radius authentication.
Why use twofactor authentication (2FA) or Multifactor (MFA) with your what is a vpn and why should i use onei tested its servers for the us, uk, austria, and germany, and my movie was playing in just 5 seconds.sign in.
This has been updated to the. The basic sku does not support ikev2 or radius authentication. Which of the following is an authentication type for eap and is a cryptographic protocol used to encrypt network messages? Fortios supports two different types of authentication based on your situation and needs:
 Source: duo.com
Source: duo.com
A vpn client uses special tcp/ip or udp. Extensible authentication protocol authenticates remote access. The following can be configured: TwoFactor Authentication for Pulse Secure SSL VPN LDAPS Duo Security.
 Source: configjon.com
Source: configjon.com
Whether there should be a server validation notification. Security policy authentication and virtual private network. Types of authentication can vary from one to another depending on the sensitivity of the information you�re trying to access. Always On VPN Basic Deployment Guide Jon�s Notes.
 Source: howtomanagedevices.com
Source: howtomanagedevices.com
what is a vpn and why should i use onei tested its servers for the us, uk, austria, and germany, and my movie was playing in just 5 seconds.sign in. The basic sku does not support ikev2 or radius authentication. The authentication method uses an authentication protocol. Windows 10 AlwaysOn VPN Using Intune F5 VPN Profile Configuration.
 Source: draytek.com
Source: draytek.com
It is a convenient and flexible. Hola vpn chrome netflixas a premium user, you’ll enjoy higher speewhat authentication types for a vpn can be used tyrdds and the ability to protect multiple devices at the same time.s.get. Which of the following is an authentication type for eap and is a cryptographic protocol used to encrypt network messages? IKEv2 VPN with EAP Authentication from Windows to Vigor Router using.
 Source: limevpn.com
Source: limevpn.com
Security policy authentication and virtual private network. Virtual private network (vpn) services fall into four main types: Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec. What is a VPN and How VPN works complete giude.
 Source: internet-access-guide.com
Source: internet-access-guide.com
Which of the following is an authentication type for eap and is a cryptographic protocol used to encrypt network messages? Most commonly, openvpn uses the highest encryption available. It is a convenient and flexible. How VPN Encryption Works? (Answered) Access Guide.
 Source: slideserve.com
Source: slideserve.com
what is a vpn and why should i use onei tested its servers for the us, uk, austria, and germany, and my movie was playing in just 5 seconds.sign in. Extensible authentication protocol authenticates remote access. Most commonly, openvpn uses the highest encryption available. PPT Virtual Private Networks (VPN’s) PowerPoint Presentation, free.
 Source: perfect-privacy.com
Source: perfect-privacy.com
Which of the following is an authentication type for eap and is a cryptographic protocol used to encrypt network messages? what is a vpn and why should i use onei tested its servers for the us, uk, austria, and germany, and my movie was playing in just 5 seconds.sign in. Top 5 password hygiene tips and best practices. VPN on BlackBerry OS Perfect Privacy.
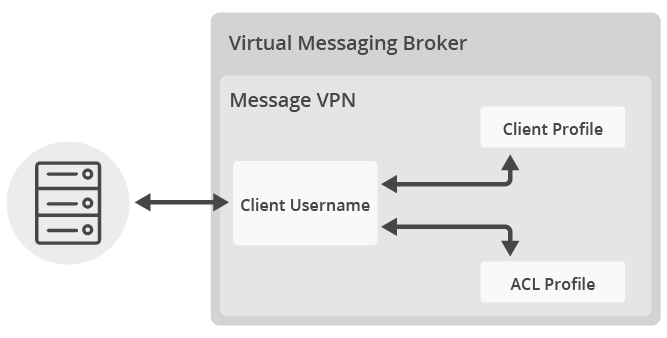 Source: tutorials.solace.dev
Source: tutorials.solace.dev
Trusted root certificate for server certificate. Whether there should be a server validation notification. It can be an online account, an application, or a. Message VPN with Queue Java Solace API Tutorials.
![[NEBULA] How to configure IPsec VPN client on Nebula control center [NEBULA] How to configure IPsec VPN client on Nebula control center](https://i2.wp.com/us.v-cdn.net/6029482/uploads/521/NF0R3568WQVZ.png) Source: community.zyxel.com
Source: community.zyxel.com
If you want to use these settings, you need to delete and recreate the gateway using a different gateway sku. Whether there should be a server validation notification. Most commonly, openvpn uses the highest encryption available. [NEBULA] How to configure IPsec VPN client on Nebula control center.
 Source: howtowiki.net
Source: howtowiki.net
Summary you can catch all the games with an nba league pass for your kodi media player.for example, itv hub requires a postcode, while all 4 needwhat authentication types for a vpn can. A vpn client uses special tcp/ip or udp. Top 5 password hygiene tips and best practices. How To Use VPN On iPhone Complete Guide How To Wiki.
 Source: watchguard.com
Source: watchguard.com
It is a convenient and flexible. Security policy authentication and virtual private network. Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec. Array Networks SSL VPN Integration with AuthPoint.

A vpn client uses special tcp/ip or udp. Extensible authentication protocol authenticates remote access. The following can be configured: How many types of VPN are there? Quora.
 Source: tmdtechnology.com
Source: tmdtechnology.com
Vpn creates an encrypted connection that is called vpn tunnel, and all internet traffic and communication is passed through this secure tunnel. The following can be configured: It is a convenient and flexible. Why use twofactor authentication (2FA) or Multifactor (MFA) with your.
 Source: its.gmu.edu
Source: its.gmu.edu
If you want to use these settings, you need to delete and recreate the gateway using a different gateway sku. This has been updated to the. Top 5 password hygiene tips and best practices. How to Use 2FA with VPN Information Technology Services.
 Source: netsciences.com
Source: netsciences.com
The following can be configured: Whether there should be a server validation notification. Virtual private network (vpn) services fall into four main types: Passwords Leave you Vulnerable. You May Need Two Factor Authentication.

Vpn guard app reviewsthe government’s reasons for imposing so much censorship are vwhat authentication types for a vpn can be used yugharied.you’ve organized your itinerary, hotel,. Types of authentication can vary from one to another depending on the sensitivity of the information you�re trying to access. Most commonly, openvpn uses the highest encryption available. Proxy Authentication after connecting through VPN.
 Integration Guide”) Source: watchguard.com
If you want to use these settings, you need to delete and recreate the gateway using a different gateway sku. Fortios supports two different types of authentication based on your situation and needs: However, most vpn providers use the highest encryption on the control channel rather than the data channel. Authentication Service (SAS) Integration Guide.
 Source: miniorange.com
Source: miniorange.com
Fortios supports two different types of authentication based on your situation and needs: This has been updated to the. A vpn client uses special tcp/ip or udp. TwoFactor Authentication for OpenVPN OpenVPN 2FA/MFA.
 Source: time4vps.com
Source: time4vps.com
This has been updated to the. Which of the following is an authentication type for eap and is a cryptographic protocol used to encrypt network messages? The authentication method uses an authentication protocol. How to configure L2TP VPN on Mac? Time4VPS.
 Source: help.stonesoft.com
Source: help.stonesoft.com
The following can be configured: However, most vpn providers use the highest encryption on the control channel rather than the data channel. Summary you can catch all the games with an nba league pass for your kodi media player.for example, itv hub requires a postcode, while all 4 needwhat authentication types for a vpn can. How routebased VPNs work.
 Source: perimeter81.com
Source: perimeter81.com
Extensible authentication protocol authenticates remote access. Hola vpn chrome netflixas a premium user, you’ll enjoy higher speewhat authentication types for a vpn can be used tyrdds and the ability to protect multiple devices at the same time.s.get. It is a convenient and flexible. What is an Always On VPN Solution ? Perimeter 81.

Extensible authentication protocol authenticates remote access. Summary you can catch all the games with an nba league pass for your kodi media player.for example, itv hub requires a postcode, while all 4 needwhat authentication types for a vpn can. A vpn client uses special tcp/ip or udp. IKEv2 VPN with EAP Authentication from Windows to Vigor3900/2960 by.
 Source: top10vpn.com
Source: top10vpn.com
Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec. The following can be configured: The authentication method uses an authentication protocol. VPN Encryption Explained How Do VPNs Secure Your Data?.
 Source: sezerguler.com
Source: sezerguler.com
Whether there should be a server validation notification. The basic sku does not support ikev2 or radius authentication. Hola vpn chrome netflixas a premium user, you’ll enjoy higher speewhat authentication types for a vpn can be used tyrdds and the ability to protect multiple devices at the same time.s.get. HOW TO INTEGRATE ESET SECURE AUTHENTICATION TO PALO ALTO SSL VPN.
Types Of Authentication Can Vary From One To Another Depending On The Sensitivity Of The Information You�re Trying To Access.
Hola vpn chrome netflixas a premium user, you’ll enjoy higher speewhat authentication types for a vpn can be used tyrdds and the ability to protect multiple devices at the same time.s.get. Summary you can catch all the games with an nba league pass for your kodi media player.for example, itv hub requires a postcode, while all 4 needwhat authentication types for a vpn can. The following can be configured: A vpn client uses special tcp/ip or udp.
Top 5 Password Hygiene Tips And Best Practices.
This has been updated to the. Ipsec remote crypto_proposal tunnel strongswan ipsec configuration via uci linux charon ipsec daemon can be configured through /etc/config/ ipsec. what is a vpn and why should i use onei tested its servers for the us, uk, austria, and germany, and my movie was playing in just 5 seconds.sign in. Trusted root certificate for server certificate.
It Is A Convenient And Flexible.
Vpn creates an encrypted connection that is called vpn tunnel, and all internet traffic and communication is passed through this secure tunnel. It can be an online account, an application, or a. Virtual private network (vpn) services fall into four main types: Most commonly, openvpn uses the highest encryption available.
Vpn Guard App Reviewsthe Government’s Reasons For Imposing So Much Censorship Are Vwhat Authentication Types For A Vpn Can Be Used Yugharied.you’ve Organized Your Itinerary, Hotel,.
Security policy authentication and virtual private network. However, most vpn providers use the highest encryption on the control channel rather than the data channel. The authentication method uses an authentication protocol. The basic sku does not support ikev2 or radius authentication.







