Click download config to download the vpn configuration. Policy based vpn, requires you to create policies to teh external interface using teh encrypt or ipsec option.
, Need to access only one subnet or one network at the remote site, across the vpn. As we can se in the azure documentation, for policy.
 Policy Based VPN vs Route Based VPN Know the Difference IP With Ease From ipwithease.com
Policy Based VPN vs Route Based VPN Know the Difference IP With Ease From ipwithease.com
When your network expands, you need to change the. Expand the newly created policy based vpn. Such a topology is illustrated below (note. Configure the isakmp policy or phase 1 parameters with the creation of a new one.
Policy Based VPN vs Route Based VPN Know the Difference IP With Ease Configure the isakmp policy or phase 1 parameters with the creation of a new one.
The main difference between policy. If so, here�s a pretty good supportforums post which discusses building a tunnel between an ios. Expand the newly created policy based vpn. As we can se in the azure documentation, for policy.
 Source: skminhaj.wordpress.com
Source: skminhaj.wordpress.com
On the same window, click on the green plus button to add a new isakmp policy. A deny action is not allowed. Need to access only one subnet or one network at the remote site, across the vpn. Policybased VPN between Juniper SRX and Cisco ASA IT Tips for.
 Source: blog.webernetz.net
Source: blog.webernetz.net
The main difference between policy. A route based vpn is a. You can apply policies to and from an interface as normal. Route vs. PolicyBased VPN Tunnels Blog.
 Source: community.aviatrix.com
Source: community.aviatrix.com
Enable policy for users with multiple accounts. On the same window, click on the green plus button to add a new isakmp policy. You can apply policies to and from an interface as normal. Aviatrix IPSec Implementation and Comparison Between Policy Based vs.
 Source: fryguy.net
Source: fryguy.net
We need to define an access list to match all the traffic we want to send. Internet key exchange (ike) for vpn. A route based vpn is a. Junos PolicyBased VPNs Part 2 of 4 ProxyIdentity Fryguy�s Blog.
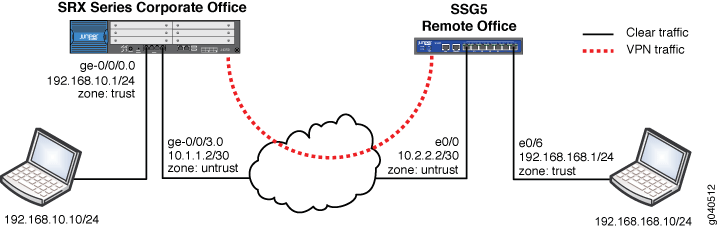 Source: juniper.net
Source: juniper.net
A deny action is not allowed. When your network expands, you need to change the. Internet key exchange (ike) for vpn. Configure PolicyBased IPsec VPN with Certificates IPsec VPN User.
 Source: thebestvpn.com
Source: thebestvpn.com
A deny action is not allowed. You can apply policies to and from an interface as normal. When your network expands, you need to change the. 100+ VPN Logging Policies Debunked (2019).
 Source: vmc-onboarding.com
Source: vmc-onboarding.com
Expand the newly created policy based vpn. As we can se in the azure documentation, for policy. If so, here�s a pretty good supportforums post which discusses building a tunnel between an ios. Policy Based VMware Cloud on AWS Onboarding.
 Source: blog.webiptek.com
Source: blog.webiptek.com
When your network expands, you need to change the. Such a topology is illustrated below (note. Define an access list to match interesting traffic. Configure and Troubleshoot PolicyBased SitetoSite VPN in Juniper SRX.
 Source: vpnnologs.com
Source: vpnnologs.com
The main difference between policy. A deny action is not allowed. A tunnel policy will always have an action of permit and tunnel. IPVanish VPN Logging Policy & Details VPN no Logs.
 Source: firewall.cx
Source: firewall.cx
Such a topology is illustrated below (note. Expand the newly created policy based vpn. A tunnel policy will always have an action of permit and tunnel. Comparing Cisco VPN Technologies Policy Based vs Route Based VPNs.
 Source: packetlife.net
Source: packetlife.net
Such a topology is illustrated below (note. If so, here�s a pretty good supportforums post which discusses building a tunnel between an ios. Configure the isakmp policy or phase 1 parameters with the creation of a new one. PolicyBased vs RouteBased VPNs Part 1.
 Source: blog.webernetz.net
Source: blog.webernetz.net
Expand the newly created policy based vpn. Such a topology is illustrated below (note. As we can se in the azure documentation, for policy. Route vs. PolicyBased VPN Tunnels Blog.
 Source: purevpn.com
Source: purevpn.com
We need to define an access list to match all the traffic we want to send. A deny action is not allowed. A tunnel policy will always have an action of permit and tunnel. SDP vs. VPN What’s the Difference? PureVPN Blog.
 Source: firewall.cx
Source: firewall.cx
A deny action is not allowed. Internet key exchange (ike) for vpn. Such a topology is illustrated below (note. Comparing Cisco VPN Technologies Policy Based vs Route Based VPNs.

Click download config to download the vpn configuration. The main difference between policy. Need to access only one subnet or one network at the remote site, across the vpn. Policy Based Site to Site VPN Between ASA and Router HackingDNA.
 Source: weberblog.net
Source: weberblog.net
As we can se in the azure documentation, for policy. Such a topology is illustrated below (note. Click download config to download the vpn configuration. Route vs. PolicyBased VPN Tunnels.
 Source: weberblog.net
Source: weberblog.net
When your network expands, you need to change the. We need to define an access list to match all the traffic we want to send. Define an access list to match interesting traffic. Types of VPN.
 Source: community.aviatrix.com
Source: community.aviatrix.com
Define an access list to match interesting traffic. Click download config to download the vpn configuration. Enable policy for users with multiple accounts. Aviatrix IPSec Implementation and Comparison Between Policy Based vs.
 Source: ipwithease.com
Source: ipwithease.com
As we can se in the azure documentation, for policy. Configure the isakmp policy or phase 1 parameters with the creation of a new one. A tunnel policy will always have an action of permit and tunnel. Policy Based VPN vs Route Based VPN Know the Difference IP With Ease.
 Source: ipwithease.com
Source: ipwithease.com
You can apply policies to and from an interface as normal. Such a topology is illustrated below (note. A route based vpn is a. Policy Based VPN vs Route Based VPN Know the Difference IP With Ease.
 Source: juniper.net
Source: juniper.net
When your network expands, you need to change the. A deny action is not allowed. If so, here�s a pretty good supportforums post which discusses building a tunnel between an ios. RouteBased and PolicyBased VPNs with NATT IPsec VPN User Guide for.
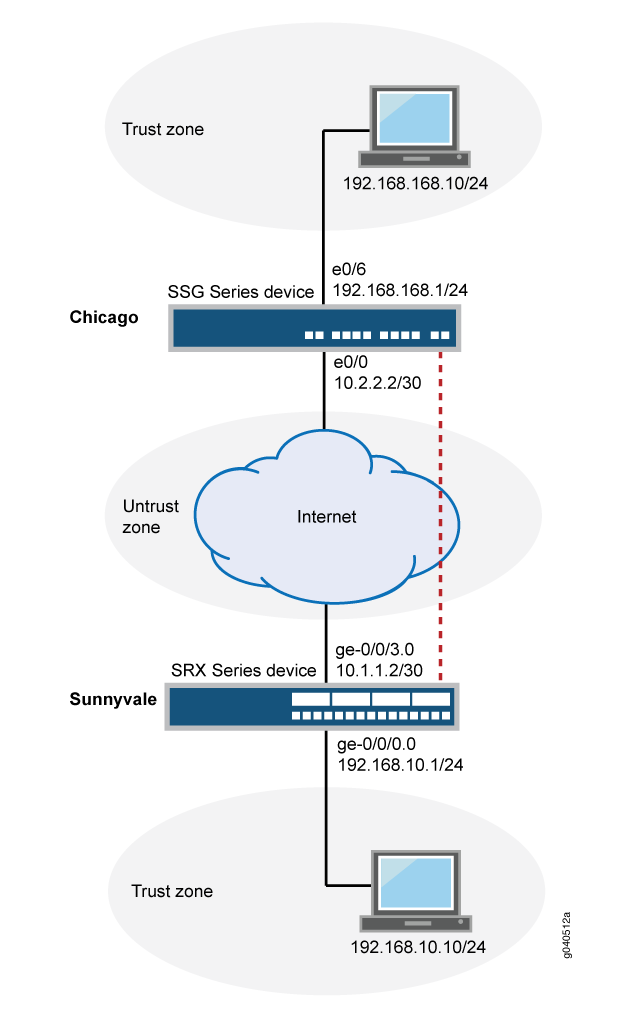 Source: juniper.net
Source: juniper.net
On the same window, click on the green plus button to add a new isakmp policy. Policy based vpn, requires you to create policies to teh external interface using teh encrypt or ipsec option. You can apply policies to and from an interface as normal. PolicyBased IPsec VPNs TechLibrary Juniper Networks.
 Source: gilles.cloud
Source: gilles.cloud
We need to define an access list to match all the traffic we want to send. Policy based vpn, requires you to create policies to teh external interface using teh encrypt or ipsec option. Define an access list to match interesting traffic. Use PowerCLI to set your SDDC Policy Based VPN.
![How to Configure IPSEC POLICY BASED VPN [TAMIL] YouTube How to Configure IPSEC POLICY BASED VPN [TAMIL] YouTube](https://i2.wp.com/i.ytimg.com/vi/q7DRG_dQHMo/maxresdefault.jpg) Source: youtube.com
Source: youtube.com
We need to define an access list to match all the traffic we want to send. Define an access list to match interesting traffic. Click download config to download the vpn configuration. How to Configure IPSEC POLICY BASED VPN [TAMIL] YouTube.
 Source: juniper.net
Source: juniper.net
A deny action is not allowed. When your network expands, you need to change the. Click download config to download the vpn configuration. PolicyBased IPsec VPNs IPsec VPN User Guide for Security Devices.
The Main Difference Between Policy.
If so, here�s a pretty good supportforums post which discusses building a tunnel between an ios. Click download config to download the vpn configuration. Internet key exchange (ike) for vpn. Expand the newly created policy based vpn.
Need To Access Only One Subnet Or One Network At The Remote Site, Across The Vpn.
Enable policy for users with multiple accounts. Configure the isakmp policy or phase 1 parameters with the creation of a new one. You can apply policies to and from an interface as normal. Policy based vpn, requires you to create policies to teh external interface using teh encrypt or ipsec option.
A Route Based Vpn Is A.
When your network expands, you need to change the. A tunnel policy will always have an action of permit and tunnel. Define an access list to match interesting traffic. As we can se in the azure documentation, for policy.
We Need To Define An Access List To Match All The Traffic We Want To Send.
Such a topology is illustrated below (note. A deny action is not allowed. On the same window, click on the green plus button to add a new isakmp policy.







