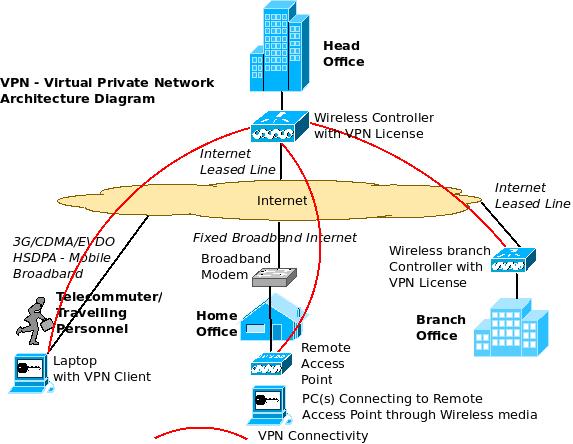
A virtual private network, better known as a vpn, gives you online privacy and anonymity by creating a private network from a public internet connection. Vpns mask your internet protocol (ip) address so your.
, A vpn protocol is the set of instructions/rules that outline how a connection should be made between your device and the vpn server. The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel that allows.

The key point to understand is that you can use a vpn for secure remote access, but not all vpns are suited to this function. A vpn provides a secure, encrypted connection between two points. To configure an access point vpn, from watchguard cloud: The apn finds the ip.
Virtual Network Peering, VPN Gateway, PointtoSite and SitetoSite The protocol determines the speed and.
Vpn stands for virtual private network. Before setting up the vpn connection for our raspberry pi access point, we have to set the pi up as an access point. Traffic is then passed over. Vpns mask your internet protocol (ip) address so your.
 Source: optace.co.ke
Source: optace.co.ke
The challenges of adding wireless to a deployment go far beyond the physical. Apn stands for access point name. Before setting up the vpn connection, the two endpoints of the connection create a shared encryption key. VPN, the Continuity Solution for your Business. Optace.
 Source: paloaltonetworks.com
Source: paloaltonetworks.com
A virtual private network, better known as a vpn, gives you online privacy and anonymity by creating a private network from a public internet connection. A vpn protocol is the set of instructions/rules that outline how a connection should be made between your device and the vpn server. The key point to understand is that you can use a vpn for secure remote access, but not all vpns are suited to this function. How to secure your remote workforce The critical role of a secure VPN.
 Source: kreyda.blogspot.com
Source: kreyda.blogspot.com
A virtual private network, better known as a vpn, gives you online privacy and anonymity by creating a private network from a public internet connection. This tunnel goes through the public internet but the data. The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel that allows. kreyda Creating Check Point VPNtunnel for Remote Access users..

A remote access virtual private network (vpn) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and. Now let’s jump to the openvpn directory where we will be storing all the stuff we need to get our raspberry pi vpn access point up and. However, this port has known vulnerabilities. What is a VPN? All you need to know about Virtual Private Networks.
 Source: update-tutorials.blogspot.com
Source: update-tutorials.blogspot.com
Vpn appliance as a single point of failure: A virtual private network (vpn) creates a secure tunnel that extends from within your company across the web. It allows you to connect your computer to a private network, creating an encrypted connection that masks your ip address to securely. update tutorials Tutorial Mikrotik VPN Point to Point Tunnel.
 Source: theconversation.com
Source: theconversation.com
The challenges of adding wireless to a deployment go far beyond the physical. Traffic is then passed over. This tunnel goes through the public internet but the data. Explainer what is a virtual private network (VPN)?.
 Source: calap.co
Source: calap.co
The access point sites page opens. Vpn appliance as a single point of failure: A mobile vpn is a network configuration in which mobile devices such as notebook computer s or personal digital assistants ( pdas ) access a. How to use Raspberry Pi 3 Model B as a VPN access point.
 Source: arubanetworks.com
Source: arubanetworks.com
Traffic is then passed over. Before setting up the vpn connection for our raspberry pi access point, we have to set the pi up as an access point. A remote access virtual private network (vpn) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and. Access Points for Secure Remote VPN Connectivity Aruba.
 Source: dzone.com
Source: dzone.com
A virtual private network (vpn) creates a secure tunnel that extends from within your company across the web. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. An access point name (apn) on mobile phones establishes a connection to the gateway between the carrier�s network and the internet. The Four Most Common VPN Protocols Explained and Compared DZone Security.
 Source: bloggingpro.com
Source: bloggingpro.com
A remote access vpn works by creating a virtual tunnel between an employee’s device and the company’s network. A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. The best option is to use the nordlayer remote. How Using a VPN Service Makes a Blogger�s Life Better.
 Source: guillermo-roman.com
Source: guillermo-roman.com
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. A mobile vpn is a network configuration in which mobile devices such as notebook computer s or personal digital assistants ( pdas ) access a. From a subscriber account, select configure > access point sites. Network Security Part 7 Remote Access & VPNs Guillermo Roman.
 Source: petenetlive.com
Source: petenetlive.com
From a subscriber account, select configure > access point sites. The encrypted connection helps ensure that sensitive data is safely transmitted. Now let’s jump to the openvpn directory where we will be storing all the stuff we need to get our raspberry pi vpn access point up and. Azure Point To Site VPN (Remote Access User VPN).
 Source: purevpn.com
Source: purevpn.com
The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel that allows. Vpn appliance as a single point of failure: A vpn provides a secure, encrypted connection between two points. Remote Access VPN Secure Your Access Point with PureVPN.
 Source: excitingip.com
Source: excitingip.com
An access point name (apn) on mobile phones establishes a connection to the gateway between the carrier�s network and the internet. Apn stands for access point name. The access point sites page opens. An Overview of Enterprise VPN Virtual Private Network.
 Source: tiptopsecurity.com
Source: tiptopsecurity.com
Apn stands for access point name. Any time a cell phone or iot device uses data, its mobile. This tunnel goes through the public internet but the data. All About VPNs « TipTopSecurity.
 Source: edimax.com
Source: edimax.com
The apn finds the ip. A virtual private network gives you online privacy and anonymity by creating a private network from a public internet connection. A virtual private network, better known as a vpn, gives you online privacy and anonymity by creating a private network from a public internet connection. AC750 DualBand WiFi Router with VPN, vAccess Point, Range Extender.

It aims to provide users a direct and protected connectivity to a. A vpn protocol is the set of instructions/rules that outline how a connection should be made between your device and the vpn server. A vpn provides a secure, encrypted connection between two points. How to configure Remote Access VPN with multiple e… Check Point.

A vpn protocol is the set of instructions/rules that outline how a connection should be made between your device and the vpn server. Any time a cell phone or iot device uses data, its mobile. This enables 24/7 secure access to central network resources from anywhere. Virtual Network Peering, VPN Gateway, PointtoSite and SitetoSite.
 Source: tiptopsecurity.com
Source: tiptopsecurity.com
Before setting up the vpn connection, the two endpoints of the connection create a shared encryption key. The encrypted connection helps ensure that sensitive data is safely transmitted. This tunnel goes through the public internet but the data. All About VPNs « TipTopSecurity.
 Source: thewindowsplus.com
Source: thewindowsplus.com
This is a popular vpn protocol and port combination type, so it can be found in many different web browsers and operating systems. Vpn appliance as a single point of failure: A remote access vpn works by creating a virtual tunnel between an employee’s device and the company’s network. What is VPN, How Virtual Private Network works Explained 2021.
 Source: itshopp.com
Source: itshopp.com
Any time a cell phone or iot device uses data, its mobile. A virtual private network, better known as a vpn, gives you online privacy and anonymity by creating a private network from a public internet connection. To configure an access point vpn, from watchguard cloud: Cisco RV110W WirelessN Router VPN Firewall 802.11n wireless access.
 Source: pimylifeup.com
Source: pimylifeup.com
The access point sites page opens. A remote access vpn works by creating a virtual tunnel between an employee’s device and the company’s network. This is a popular vpn protocol and port combination type, so it can be found in many different web browsers and operating systems. Raspberry Pi VPN Access Point Setup a Basic VPN Router Pi My Life Up.
 Source: joe.blog.freemansoft.com
Source: joe.blog.freemansoft.com
Any time a cell phone or iot device uses data, its mobile. A vpn provides a secure, encrypted connection between two points. From a subscriber account, select configure > access point sites. Azure Point to Site VPN private access to your cloud environment.
 Source: hackzone.in
Source: hackzone.in
It allows you to connect your computer to a private network, creating an encrypted connection that masks your ip address to securely. A remote access vpn works by creating a virtual tunnel between an employee’s device and the company’s network. Vpn stands for virtual private network. What is the VPN? Explained Hack Zone.
 Source: sysadm.pp.ua
Source: sysadm.pp.ua
The protocol determines the speed and. It’s a gateway between a cellular network and the internet. To configure an access point vpn, from watchguard cloud: Установка и настройка OpenVPN в pointtopoint режиме.
This Enables 24/7 Secure Access To Central Network Resources From Anywhere.
It allows you to connect your computer to a private network, creating an encrypted connection that masks your ip address to securely. Apn stands for access point name. This is a popular vpn protocol and port combination type, so it can be found in many different web browsers and operating systems. A virtual private network (vpn) creates a secure tunnel that extends from within your company across the web.
A Remote Access Vpn Works By Creating A Virtual Tunnel Between An Employee’s Device And The Company’s Network.
It’s a gateway between a cellular network and the internet. From a subscriber account, select configure > access point sites. Traffic is then passed over. The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel that allows.
The Access Point Sites Page Opens.
A virtual private network, or vpn, is an encrypted connection over the internet from a device to a network. A vpn provides a secure, encrypted connection between two points. An access point name (apn) on mobile phones establishes a connection to the gateway between the carrier�s network and the internet. A vpn protocol is the set of instructions/rules that outline how a connection should be made between your device and the vpn server.
The Key Point To Understand Is That You Can Use A Vpn For Secure Remote Access, But Not All Vpns Are Suited To This Function.
The apn finds the ip. It aims to provide users a direct and protected connectivity to a. Now let’s jump to the openvpn directory where we will be storing all the stuff we need to get our raspberry pi vpn access point up and. The best option is to use the nordlayer remote.