Consequentially, we have prepared a list of vpn protocols adopted by many vpn service providers: Depending on the level of security needed, vpn.
, Ssh (secure shell) is a secure and acceptable alternative to telnet. Therefore, it is much more secure and a better option than many other vpn protocols, particularly the pptp protocol.

The strengths of using a vpn are: Sstp gets configured with aes encryption. Ssl was originally developed by netscape back in 1995 to. Ssl was originally developed by netscape back in 1995 to.
How to Configure Remote access SSL VPN for Macintosh OS X using Before we dive into protocols lets take a quick history lesson (this will help in regard to conceptualizing the information.):
While the latter are the most widespread, both technologies provide mechanisms that ensure. Those protocols are standardized and. The server sends back the singed certificate with the public key. Openvpn is an ssl vpn that uses ssl/tls for key exchange.
 Source: slideshare.net
Source: slideshare.net
The server sends back the singed certificate with the public key. Not only is tls more secure. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443 outbound, which tls uses. SSL Communication and Mutual Authentication.
 Source: pinterest.com
Source: pinterest.com
Whether there should be a server validation notification. Those protocols are standardized and. Trusted root certificate for server certificate. TLS/SSL message sequence Full TLS Handshake Ssl, Messages, It works.

Openvpn is an ssl vpn that uses ssl/tls for key exchange. Then, after a tcp connection has established, comes the ssl part: Trusted root certificate for server certificate. Explain Ssl Protocol In Detail lbdesign25.
 Source: slideserve.com
Source: slideserve.com
Customers often wonder why they should choose ipsec vpns over ssl/tls vpns. Using ssl/tls, a vpn connection is established between the user�s web browser and the vpn server, with access restricted to just specific apps rather than being available to. Ssh (secure shell) is a secure and acceptable alternative to telnet. PPT Security 1 ( IntSi1 ) PowerPoint Presentation ID2382691.
 Source: fptwaze.com
Source: fptwaze.com
Sstp gets configured with aes encryption. Depending on the level of security needed, vpn. Tls tunnel is a free vpn that aims to cross barriers imposed by internet providers and governments, and to guarantee privacy, freedom and anonymity to users. What is VPN? Pros and cons of VPN FPTwaze.
 Source: fptwaze.com
Source: fptwaze.com
Another types of protocols of vpn is sstp , secure socket tunneling protocol (sstp) is a form of vpn tunnel that provides a mechanism to transport ppp or l2tp traffic. Ipsec is often used to refer. Consequentially, we have prepared a list of vpn protocols adopted by many vpn service providers: What is VPN? Pros and cons of VPN FPTwaze.
 Source: medium.com
Source: medium.com
It relies extensively on the openssl library , as well as the tls protocol. The primary differences between ssl and tls or ssl tls are hard to detect. Consequentially, we have prepared a list of vpn protocols adopted by many vpn service providers: Deep Dive into TLS. How exactly are secure connections made… by Tj.
 Source: thecsetech.com
Source: thecsetech.com
The following can be configured: Whether there should be a server validation notification. Though not specifically a vpn protocol, this is the type of encryption most people are familiar with. Virtual Private Network (VPN).
 Source: thealmostdone.com
Source: thealmostdone.com
Openvpn is an ssl vpn that uses ssl/tls for key exchange. One of the protocols used is transport layer security (tls). Tls tunnel is a free vpn that aims to cross barriers imposed by internet providers and governments, and to guarantee privacy, freedom and anonymity to users. A Quick Guide to SSL and TLS Protocols.

Ssh (secure shell) is a secure and acceptable alternative to telnet. What’s more, recent versions of tls also offer performance benefits and other improvements. Depending on the level of security needed, vpn. How to Configure Remote access SSL VPN for Macintosh OS X using.
 Source: triella.com
Source: triella.com
Sstp gets configured with aes encryption. After sslv3, ssl was renamed to tls. Tls is a cryptographic protocol that provides privacy and data integrity between two communicating applications. Using VPN to access your computer from home Triella.
 Source: sengxay.blogspot.com
Source: sengxay.blogspot.com
Ssh allows for secure interactive control of remote systems. Those protocols are standardized and. Though not specifically a vpn protocol, this is the type of encryption most people are familiar with. Secure Sockets Layer (SSL) ແມ່ນຫຍັງ? ເຮັດວຽກແນວໃດ?.
 Source: websecurity.digicert.com
Source: websecurity.digicert.com
Trusted root certificate for server certificate. Sstp clients can optionally be authenticated during the ssl/tls phase and must be authenticated in the ppp/l2tp phase. Sstp gets configured with aes encryption. How does SSL work? What is an SSL handshake? DigiCert.
 Source: watchguard.com
It relies extensively on the openssl library , as well as the tls protocol. Ssl was originally developed by netscape back in 1995 to. Openvpn encryption can be considered. SSL/TLS Settings Precedence and Inheritance.
 Source: learnitwithcifelli.com
Source: learnitwithcifelli.com
Consequentially, we have prepared a list of vpn protocols adopted by many vpn service providers: What’s more, recent versions of tls also offer performance benefits and other improvements. Depending on the level of security needed, vpn. Basic Clientless TLS VPN on ASA.
 Source: medium.com
Source: medium.com
Tls tunnel is a free vpn that aims to cross barriers imposed by internet providers and governments, and to guarantee privacy, freedom and anonymity to users. Sstp gets configured with aes encryption. Depending on the level of security needed, vpn. An overview of the SSL Handshake Robert van Rijn Medium.
 Source: blog.crashtest-security.com
However, here are the noteworthy. Customers often wonder why they should choose ipsec vpns over ssl/tls vpns. Those protocols are standardized and. What is TLS, SSL, HTTP, and HTTPS? And how do they work together?.
 Source: johnvidler.co.uk
Source: johnvidler.co.uk
Pptp, l2tp/ipsec, ikev2/ipsec, openvpn, sstp, wireguard, softether,. Here are five common protocols (and one bonus protocol you may not know about). Another types of protocols of vpn is sstp , secure socket tunneling protocol (sstp) is a form of vpn tunnel that provides a mechanism to transport ppp or l2tp traffic. Creating VPNs with IPsec and SSL/TLS.
 Source: slideshare.net
Source: slideshare.net
Then, after a tcp connection has established, comes the ssl part: Tls tunnel is a free vpn that aims to cross barriers imposed by internet providers and governments, and to guarantee privacy, freedom and anonymity to users. Many vpn protocols do use tls. Ipsec vpn v0.1.
 Source: slideshare.net
Source: slideshare.net
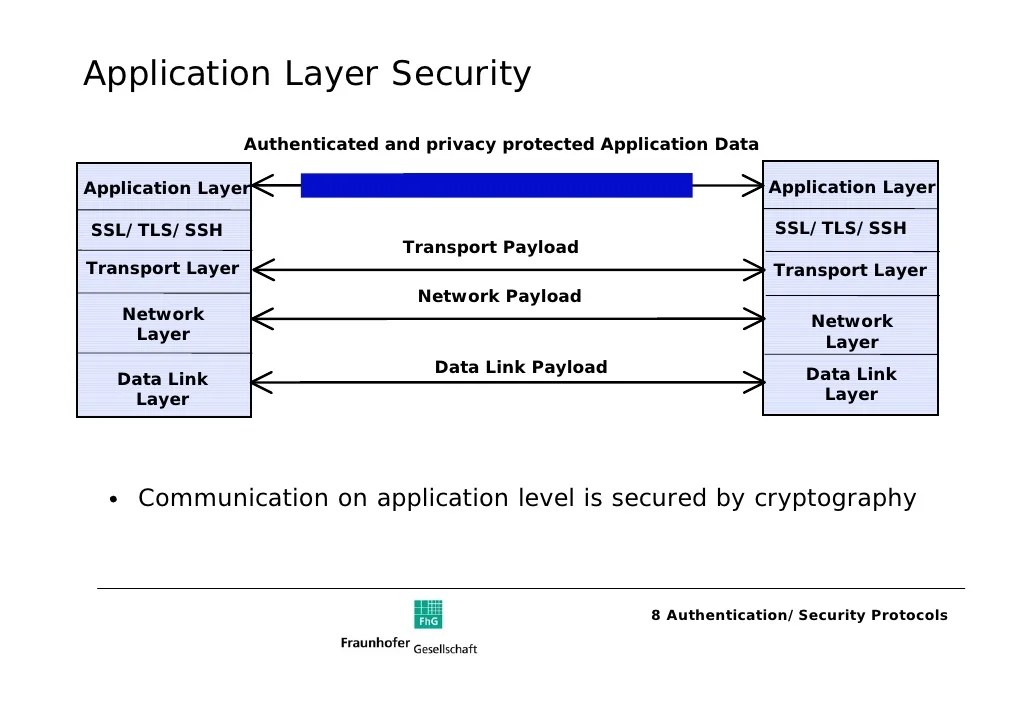
Besides ipsec vpn, vpn providers can also use ssl vpn to secure your connection over the internet. Vpn protocols determine exactly how data is routed through a connection. The data that passes through the tunnel is protected from external. 8 Authentication Security Protocols.
 Source: myrasecurity.com
Source: myrasecurity.com
Whether there should be a server validation notification. Another types of protocols of vpn is sstp , secure socket tunneling protocol (sstp) is a form of vpn tunnel that provides a mechanism to transport ppp or l2tp traffic. Though not specifically a vpn protocol, this is the type of encryption most people are familiar with. SSL what is Secure Sockets Layer? Myra.
 Source: campus.barracuda.com
Source: campus.barracuda.com
Ssl/tls vpn gateways can have a positive impact on the application servers inside your private network. Ssh (secure shell) is a secure and acceptable alternative to telnet. Ssh uses rsa public key cryptography for both. 7.2.0 EA1 Release Notes Barracuda Campus.
 Source: nginx.com
Source: nginx.com
Openvpn is an ssl vpn that uses ssl/tls for key exchange. Ssh allows for secure interactive control of remote systems. Before we dive into protocols lets take a quick history lesson (this will help in regard to conceptualizing the information.): SSL/TLS Offloading, Encryption, and Certificates with NGINX.
 Source: blog.cloudflare.com
Source: blog.cloudflare.com
Sstp gets configured with aes encryption. The following can be configured: After sslv3, ssl was renamed to tls. Protecting web origins with Authenticated Origin Pulls.
 Source: computersecuritypgp.blogspot.in
Source: computersecuritypgp.blogspot.in
Therefore, it is much more secure and a better option than many other vpn protocols, particularly the pptp protocol. Like other protocols, sstp establishes an encrypted tunnel between a vpn client and a vpn server. Many vpn protocols do use tls. Computer Security and PGP What Is Secure Sockets Layer Virtual Private.
The Primary Differences Between Ssl And Tls Or Ssl Tls Are Hard To Detect.
Depending on the level of security needed, vpn. The server sends back the singed certificate with the public key. Not only is tls more secure. While the latter are the most widespread, both technologies provide mechanisms that ensure.
Openvpn Is An Ssl Vpn That Uses Ssl/Tls For Key Exchange.
Vpn protocols determine exactly how data is routed through a connection. The strengths of using a vpn are: Pptp, l2tp/ipsec, ikev2/ipsec, openvpn, sstp, wireguard, softether,. Those protocols are standardized and.
Customers Often Wonder Why They Should Choose Ipsec Vpns Over Ssl/Tls Vpns.
Tls, the more modern version of ssl, is secure. Ssh allows for secure interactive control of remote systems. Whether there should be a server validation notification. Tls stands for transport layer security and started with tlsv1.0 which is an upgraded version of sslv3.
Used To Connect A Laptop Remotely To A Corporate Network) Support Tls As A.
An extra layer of protection. Ssh uses rsa public key cryptography for both. The data that passes through the tunnel is protected from external. It relies extensively on the openssl library , as well as the tls protocol.







